I recently had a need to run metasploit on the public internet. I needed it to be available on the public internet, but only for an hour here and there. So I decided to use Amazon’s EC2 cloud. For Amazon’s EC2 cloud, I could just run it for an hour and only pay for that much time. It is also very easy to setup and teardown servers. The downside is you can’t just install Backtrack. There are only certain templates for servers available.
Start out
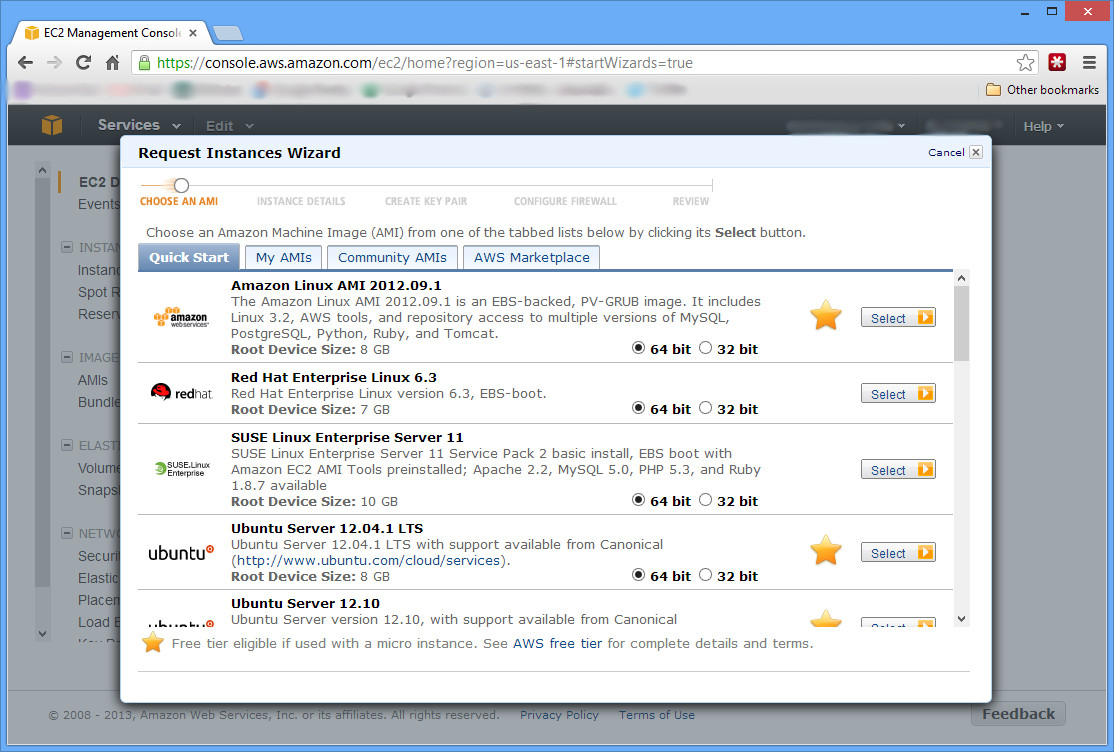
Go to Amazon’s website, and (if necessary) create an AWS (Amazon Web Services) account by clicking Sign Up. Or simply login and go to the EC2 console (you can get there from the AWS Management Console). Under the Create Instance heading, click the Launch Instance button.
Continue with the Classic Wizard, and under the Quick Start tab, select the Ubuntu Server AMI (Amazon Machine Image). The next screen lets you choose your Instance Type. If you’re planning on using your AWS free trial, you should choose the T1 Micro instance with 613 MB RAM. However, this will be difficult at best; you will have issues with too little RAM as you will see later. A good choice is the next tier up, M1 Small with 1.7 GB RAM. At only 6 cents per hour, it literally will only cost you pennies if you don’t need to run it 24/7.
Continue through all the rest of the screens, creating a key pair for login, naming your instance whatever you want, and configuring your firewall aka security group. On the firewall, by default only port 22 is allowed. Depending on how you are going to use this machine, you’ll need to add additional ports. Finally, launch!
Once you launch, your machine will be built usually within a few seconds. If you go down to the Elastic IPs section, you can first Allocate New Address to your account, and then Associate Address to your Instance that you just created. Give that about 60 seconds to associate, and then you can SSH to your Instance using that IP address with the key pair that you created during setup. The username will be ubuntu. You can also connect to the machine without associating an IP address by clicking on it on the Instance page, and connecting to the Public DNS listed under Description.
Now to install metasploit. Go to the metasploit download page, and copy the link. We’ll be installing a few packages that metasploit needs, and then installing metasploit itself.
wget http://downloads.metasploit.com/data/releases/metasploit-latest-linux-x64-installer.run
sudo apt-get update
sudo apt-get install postgreSQL rubygems libpq-dev libreadline-dev ruby-dev
sudo ./metasploit-latest-linux-x64-installer.run
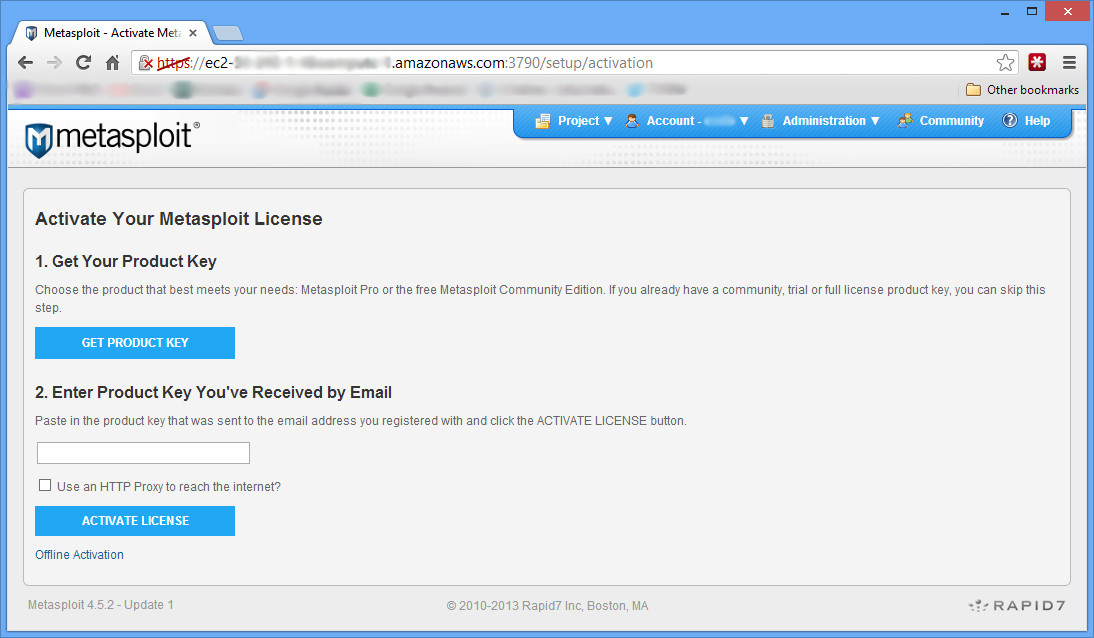
Just choose all the defaults with the installer. When it is done, you’ve got Metasploit installed and working (msfconsole should work). However you can’t run updates until you register it. In order to register it, the install wants you to go to https://localhost:3790. However this is a remote install; there is no easy way to do that. So go to https://INSTANCEIP:3790/ and as the screen says, wait a few mins for metasploit to finish loading. Once it does, you’ll get a screen that says you need to connect locally, or use a special script to create a user account. This is what we are going to do:
cd /opt/metasploit
sudo ./diagnostic_shell
ruby /opt/metasploit/apps/pro/ui/script/createuser
With your user created, refresh the page on your browser and login. From there, just follow the instructions to get a (free) license key for the community version and register. Now updating and running should work just fine!
Now at this point, if you chose the trial Micro instance instead of the 6 cent Small instance, you are probably getting a message that says “Activation Failed: Cannot allocate memory – who”. Just like it says, that means there is not enough RAM. You’ll either have to just live without any updates, or start over again with a better instance.
If you plan on penetration testing with the Amazon Cloud, you can do it, but you need to fill out a form with them (and use something better than the Small or Micro instances).