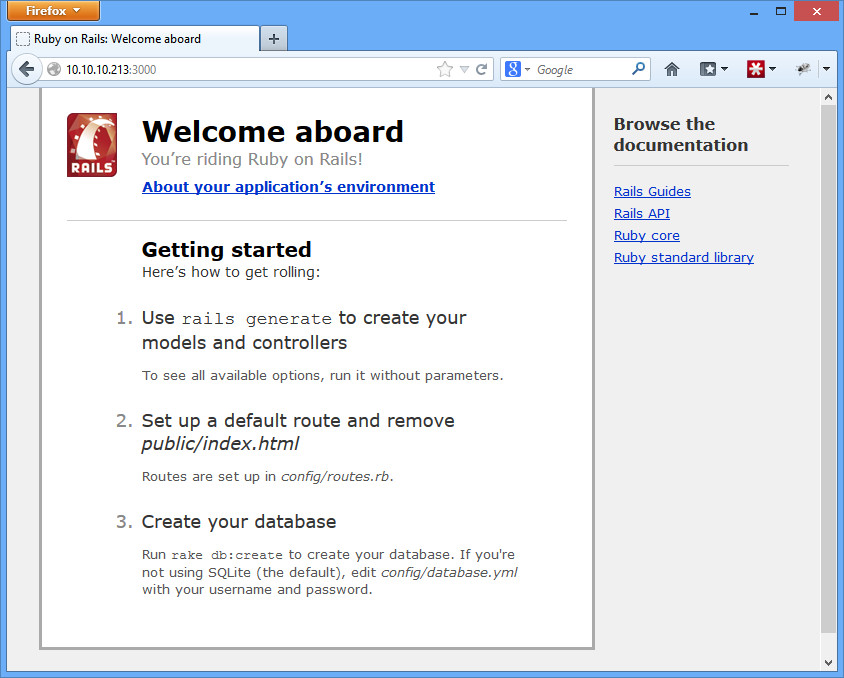
I recognized my post about the ruby on rails vulnerability as a good opportunity to bring up shodan.
Shodan is a unique search engine. It crawls the web for the banners listed at various ports. Mainly it grabs and indexes HTTP headers, but it does a few other ports and protocols as well. At first, this doesn’t sound incredibly exciting, but if you think about it, you’ll see the tremendous potential this has as a passive reconnaissance tool.
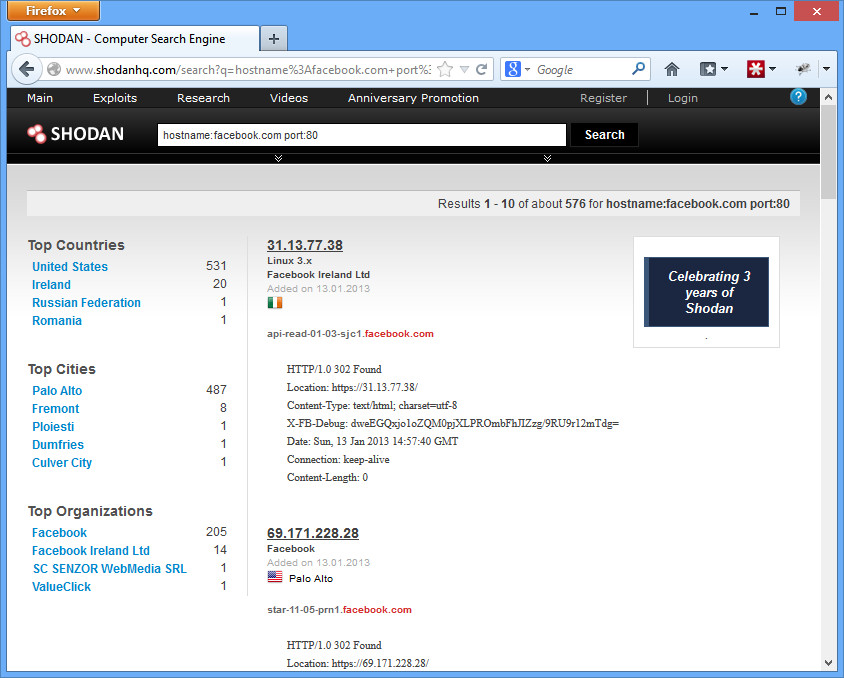
For example, if you want to start finding all of Facebook.com’s IP space, you can do so with the query “hostname:facebook.com port:80”
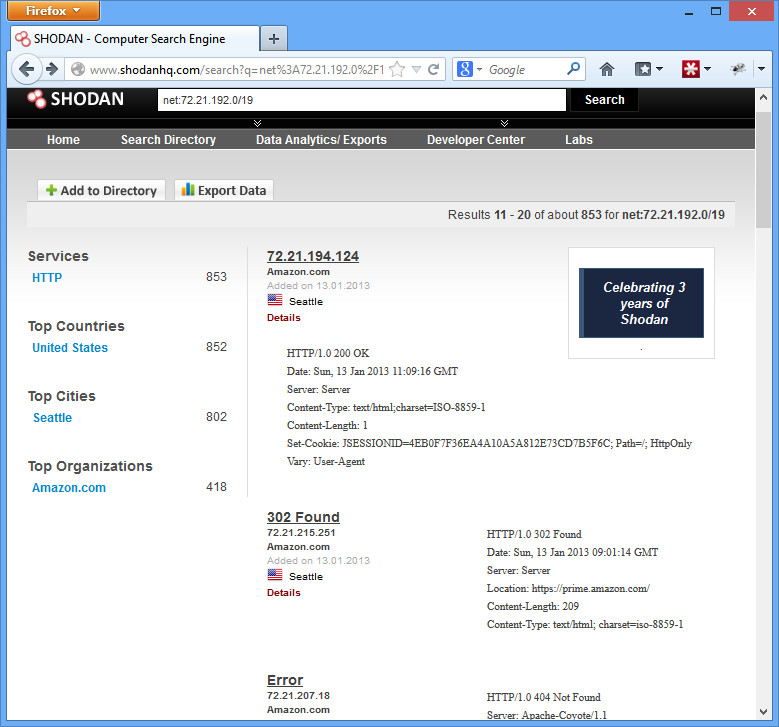
 Or you can research and see just what kind of fingerprint your corporation has on the web. Say, for example, you work for Amazon and you want to see what kinds of things are found externally on a set of your IP addresses. You’d search for “net:72.21.192.0/19”
Or you can research and see just what kind of fingerprint your corporation has on the web. Say, for example, you work for Amazon and you want to see what kinds of things are found externally on a set of your IP addresses. You’d search for “net:72.21.192.0/19”
You can see that there are lots of HTTP services open, and a lot of them are using the AmazonS3 web server with some Apache stuff sprinkled in. Nothing surprising, but you’re able to begin to fingerprint what kinds of systems Amazon runs.
Moving back to the ruby on rails example. We know that systems 3.2.10 and earlier are vulnerable. Our particular default install used a unique sounding web server called WEBrick. What if we search for that?
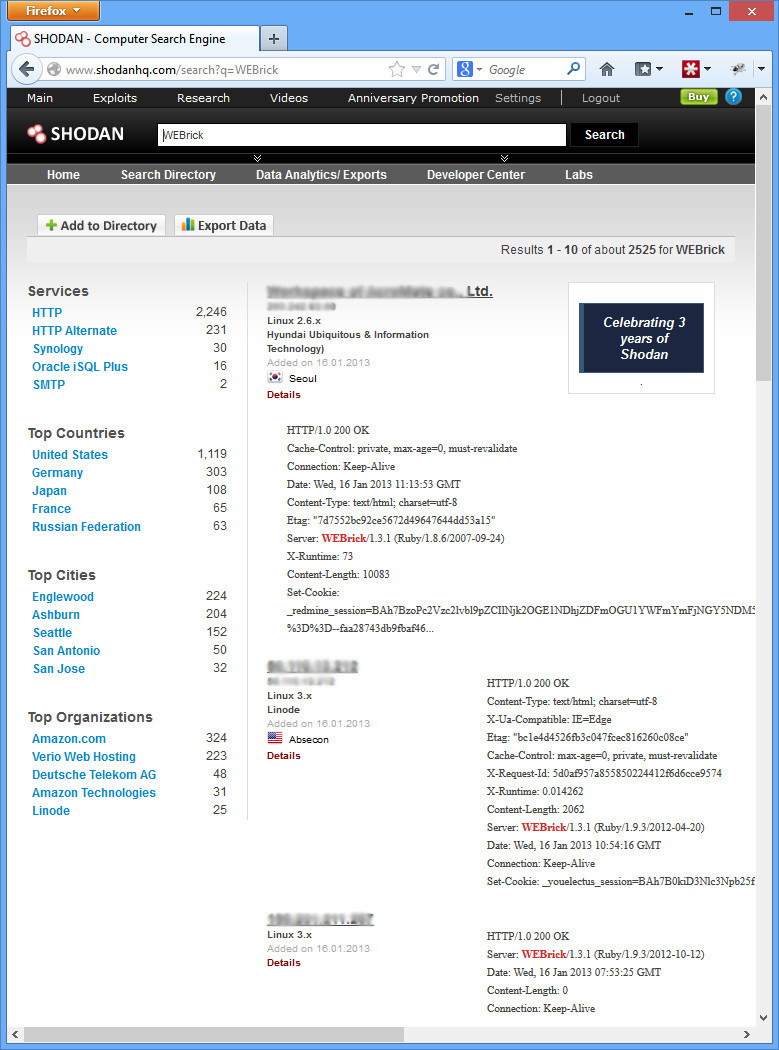 Now we’re getting somewhere. Over 2000 hits with our first search, and most appear to be Ruby on Rails. Now let’s verify it’s a vulnerable version. I just took the 2nd IP down, opened it up, and added the path for the defaults rails about page (http://IP/rails/info/properties). Here’s what I got:
Now we’re getting somewhere. Over 2000 hits with our first search, and most appear to be Ruby on Rails. Now let’s verify it’s a vulnerable version. I just took the 2nd IP down, opened it up, and added the path for the defaults rails about page (http://IP/rails/info/properties). Here’s what I got:
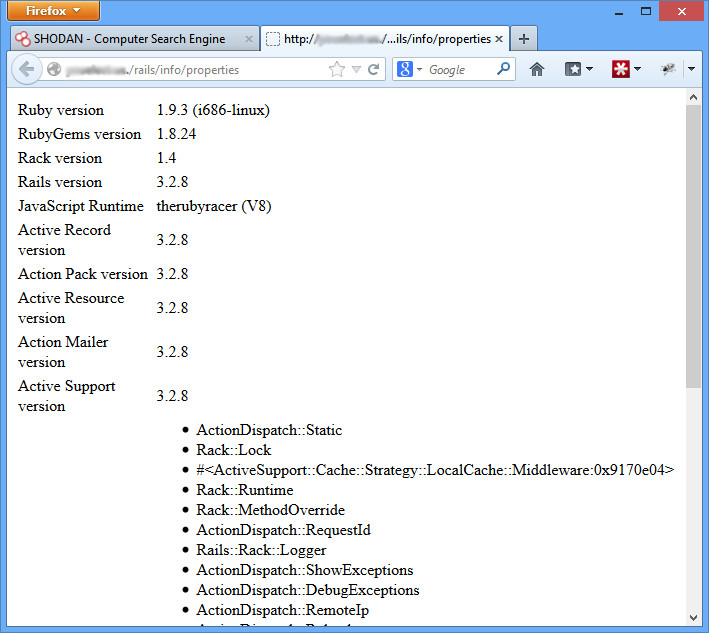 Rails version 3.2.8. Definitely vulnerable. We could pwn this box right now, easy. But we don’t have any kind of rules of engagement or agreement with these people, so we don’t. And chances are, they are already pwned. We could send them a quick e-mail letting them know they are in serious trouble, or even see if they have a bug bounty. Or try to get a job, since their security guys obviously are lacking.
Rails version 3.2.8. Definitely vulnerable. We could pwn this box right now, easy. But we don’t have any kind of rules of engagement or agreement with these people, so we don’t. And chances are, they are already pwned. We could send them a quick e-mail letting them know they are in serious trouble, or even see if they have a bug bounty. Or try to get a job, since their security guys obviously are lacking.
Don’t want this to be you, an easily recognizable target? Search for your corporation and make sure you are safe.
This is only touching the surface of what shodan does. There’s a great video located here which talks about more, including finding default passwords on systems, etc. just with the header information. Happy hunting!