To understand X11 and some other ways to attack it, see the first X11 post.
There are a few additional things you can do with open X11 ports, but they don’t seem to work on a Ubuntu system. Therefore I am setting up a CentOS 6.4 machine for this next test.
Setup Your Testbed
Run the default install of CentOS. I used the LiveCD and ran the installer from there.
Once CentOS is installed, make sure you either disable the firewall or add in the appropriate ports. Otherwise you’ll spend a long time troubleshooting why those ports don’t appear to be open over the network. You can do this either from the GUI (System -> Administrator -> Firewall), or the GUI (/etc/init.d/iptables stop)
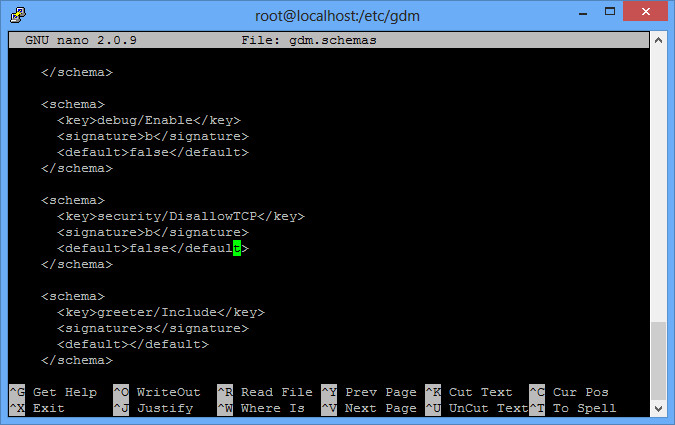
Allowing direct TCP connection to X11 is done by editing the /etc/gdm/gdm.schemas file. There is an option called security/DisallowTCP that needs to be changed from true to false.
After this, restart your X server (or the entire system) and you should have port 6000 open. If not, check the firewall again (iptables -L should either be empty, or have a rule for dst port 6000 BEFORE any deny all rule).
Also, remember to follow the same procedure as listed in the last X11 post. xhost + must be added so that anyone can connect.
Attack
How do you find a vulnerable host?
This section is the same as the last X11 post.
How do you attack that host?
Double check to make sure the previous attacks work (such as grabbing a screen shot).
The first thing we are going to do is setup a keylogger over X11. Download the xkey.c file from here. Then compile it just as it mentions in the instructions:
root@kali:~# gcc -o xkey xkey.c -lX11 -lm
xkey.c: In function `main`:
xkey.c:81:6: warning: incompatible implicit declaration of built-in function `exit` [enabled by default]
There will be some warnings as shown above, but no errors – the program compiles just fine. Then you just simply need to run the program in the form ./xkey <ip address>:<x11 number>. So run the following:
# ./xkey 192.168.1.5:0
Then start typing on your CentOS box. The key presses will pop up.
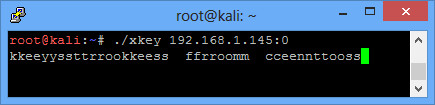 Note: I really don’t know why everything is doubled up, but the point is, keystrokes are being logged.
Note: I really don’t know why everything is doubled up, but the point is, keystrokes are being logged.
By the way, I’ve also been playing with some older tools that are supposed to be able to push commands over X11 (like what we were doing with xdotool). They are called xpusher.c and xtester.c. I haven’t gotten them to work yet though – if anyone else has, please comment.