Metasploitable 2 (even better than the original Metasploitable) is a great way to practice your hacking skills. I use it all the time for my sandbox setup phase.
Metasploitable 2 also comes with several vulnerable websites to practice your web exploitation skills. My favorite is Mutillidae. However, there is a small error in the Mutillidae setup on Metasploitable 2. Thankfully, it is easily fixable.
The problem is that the database specified in the Mutillidae config file is incorrect. You will know you are experiencing this problem if you click on something that requires the database and you get a bunch of header errors that don’t look quite right.
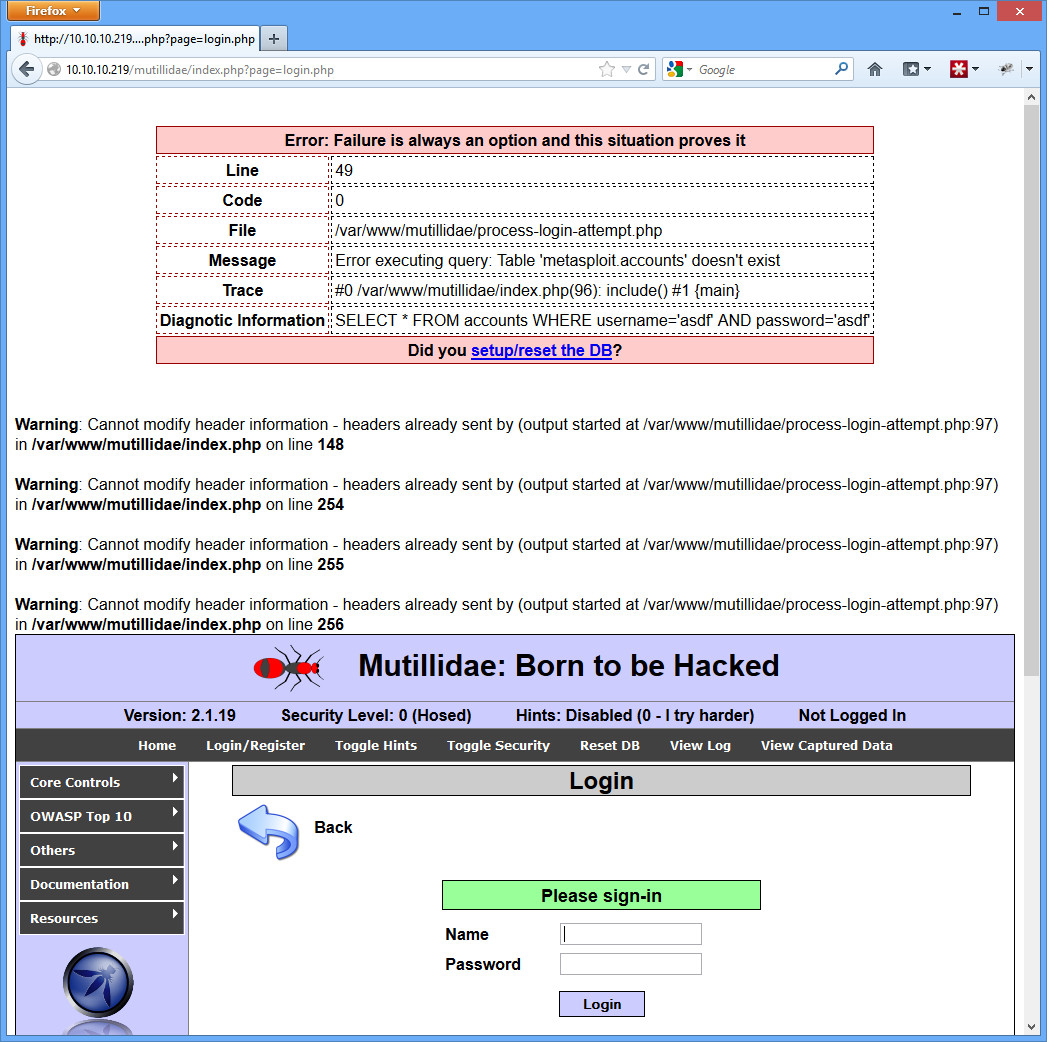 In the example above, I simply clicked the Login/Register button on the top bar, typed something in for the username and password, and clicked Login.
In the example above, I simply clicked the Login/Register button on the top bar, typed something in for the username and password, and clicked Login.
To fix it, log into Metasploitable 2 (msfadmin/msfadmin), and open up the /var/www/mutillidae/config.inc file (you may need to use sudo). Change the dbname field from “metasploit” to “owasp10”. Save it, and try the login page again.
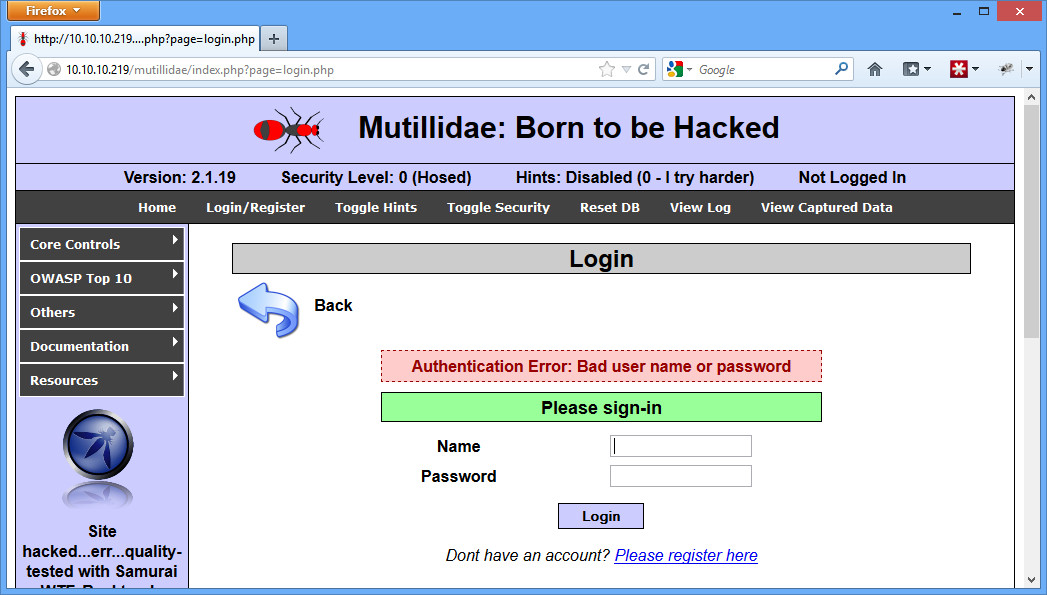
 You should get just a simple authentication error:
You should get just a simple authentication error:
 Now you’re good to go with Mutillidae and Metasploitable 2!
Now you’re good to go with Mutillidae and Metasploitable 2!
I upgraded to Mutillidae 2.6.2 on Metasploitable 2 recently. I am trying to do sql injection on Kali Linux from the Kali box to Metasploitable 2 box on the following page http://192.168.1.104/mutillidae/index.php?page=user-info.php.
I get an error message when I have a syntax error in my query in the “Name” input box. For example if I type “‘ union select null,VERSION() AS username,null,null — “I get an error message which gives me relevant information which is what I would expect. If I type “‘ union select null,VERSION() AS username,null,null,null — ” which has one more column I get rid of the error message but get “0 records found.” I know the “nowasp” database is on Metasploitable 2 because I was able to access it using “mysql” query commands and viewed passwords, usernames etc. I have checked the “/var/www/mutillidae/classes/MySQLHandler.php” file using the “vim” command and it appears to be configured properly. I am not sure why these queries will not work. I tried the “sqlmap” tool against the database using “sqlmap -u http://192.168.1.104/mutillidae/index.php?page=user-info.php –forms –batch -D nowasp -T accounts –dump” and it told me that “username” and “password” are not injectable. Since Mutillidae is set up to be injectable on Security Level 0 it should work I think.
I can perform other exploits on Mutillidae 2.6.2 such as command injection. For example the “;ls” command on the “DNS Lookup” page gives me a listing of files in the current directory of Metasploitable 2.Likewise “; cat /etc/passwd” gives me a listing of usernames and passwords. The problem is the sql injection. I must need to configure something differently but I can’t figure it out. Has anyone else run into this issue? I had not issues with sql injection on the earlier version of Mutillidae using the same procedures as above.
Thank you! This was annoying me so much! But this worked