The last post on exploit kits caused me to look into BeEF. At first glance, BeEF appears to be an open source browser exploit kit. With a little more work, perhaps it could be just that, but it is not quite there. It sure is a neat tool, though, and I’d like to try integrating it into some of my own engagements in the future. Lets look at it.
Setup BeEF
The tool is already built into Backtrack under /pentest/web/beef. First you’ll want to enable the metasploit module by editing the /pentest/web/beef/config.yaml file and change the metasploit enable line from false to true:
Then launch metasploit (msfconsole) and start up the API for BeEF to connect to:
load msgrpc ServerHost=127.0.0.1 Pass=abc123
Finally go ahead and start the BeEF server:
# cd /pentest/web/beef
# ./beef
[14:08:02][*] Browser Exploitation Framework (BeEF)
[14:08:02] | Version 0.4.3.6-alpha
[14:08:02] | Website http://beefproject.com
[14:08:02] | Run 'beef -h' for basic help.
[14:08:02] |_ Run 'git pull' to update to the latest revision.
[14:08:02][*] Successful connection with Metasploit.
[14:08:05][*] Loaded 226 Metasploit exploits.
[14:08:05][*] BeEF is loading. Wait a few seconds...
[14:08:06][*] 9 extensions loaded:
[14:08:06] | Demos
[14:08:06] | Autoloader
[14:08:06] | Events
[14:08:06] | XSSRays
[14:08:06] | Requester
[14:08:06] | Metasploit
[14:08:06] | Console
[14:08:06] | Admin UI
[14:08:06] |_ Proxy
[14:08:06][*] 339 modules enabled.
[14:08:06][*] 2 network interfaces were detected.
[14:08:06][+] running on network interface: 127.0.0.1
[14:08:06] | Hook URL: http://127.0.0.1:3000/hook.js
[14:08:06] |_ UI URL: http://127.0.0.1:3000/ui/panel
[14:08:06][+] running on network interface: 192.168.1.6
[14:08:06] | Hook URL: http://192.168.1.6:3000/hook.js
[14:08:06] |_ UI URL: http://192.168.1.6:3000/ui/panel
[14:08:06][*] RESTful API key: 00f4d61986f5adeed4fec94a4eb15da9a8b4c449
[14:08:06][*] HTTP Proxy: http://127.0.0.1:6789
[14:08:06][*] BeEF server started (press control+c to stop)
Using BeEF
The tool has documentation on the wiki here. The documentation is pretty minimal, but for the most part you can figure it out.
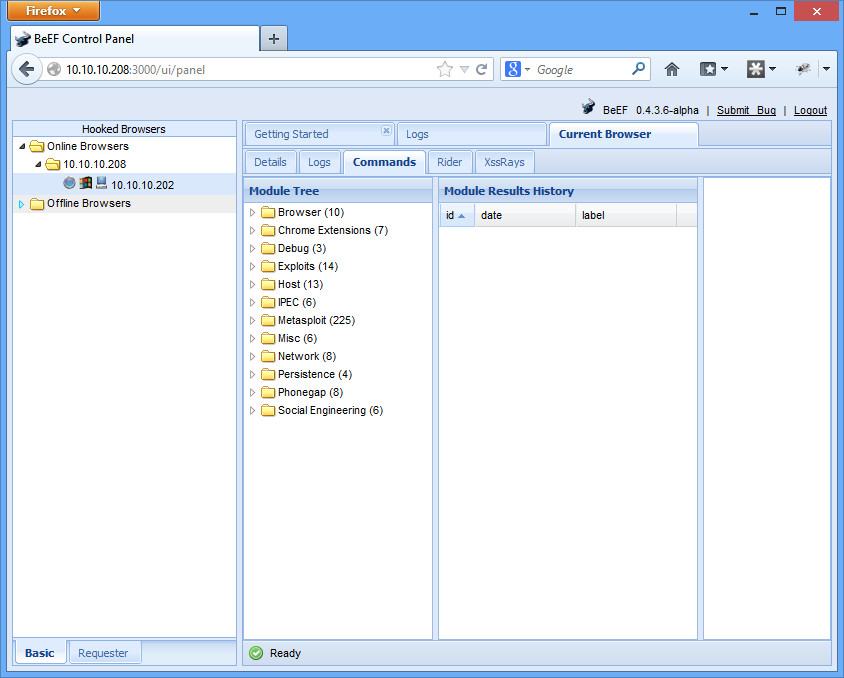
Then you can browse to the admin panel at http://192.168.1.6:3000/ui/panel. The username and password by default is beef/beef (as specified in the config.yaml file).
Now you need to “hook” a browser. Simply browse with any web browser to http://192.168.1.6:3000/demos/basic.html or http://192.168.1.6:3000/demos/butcher/index.html. You’ll see the browser pop up right away on the admin panel, with different exploits based on modules that you can run on the “Commands” tab:
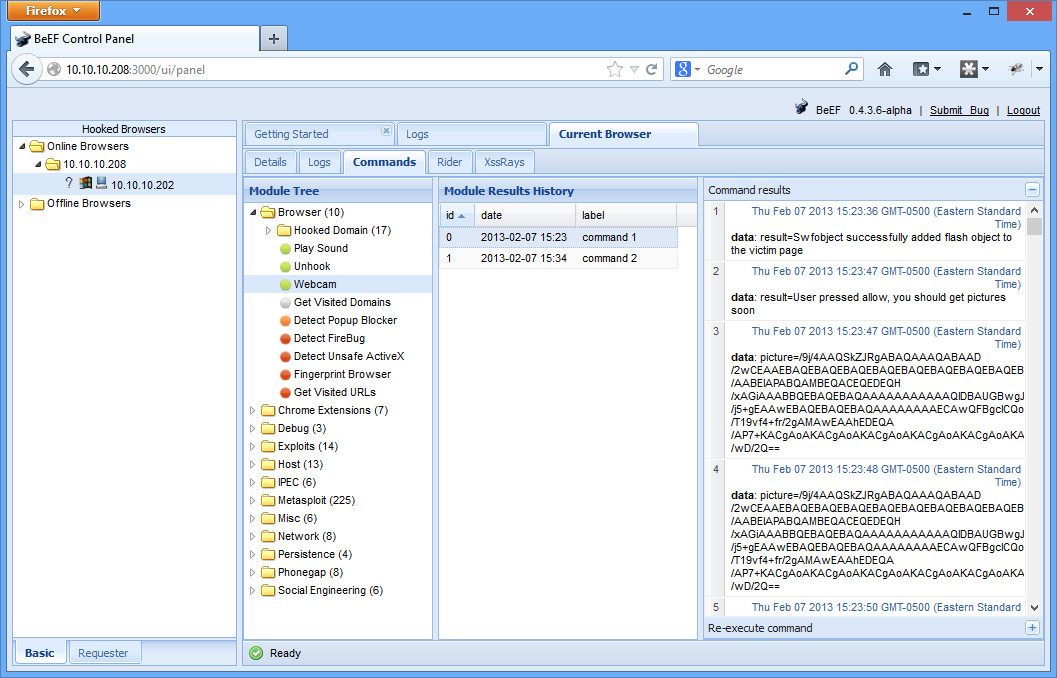
There is all sorts of little information gathering tidbits you can grab. One neat module is under Browser, you can grab some webcam pictures. Once you execute it, your basic.html page automagically changes (give it a minute), asking for permission to run the webcam. Eventually, you’ll be able to click on the “Module Results History” tab, and you’ll see a base64 encoded version of your image pop up (picture=/9j/4AA….)
Copy the base64 text into a file called picture.txt (it’ll start with /9y/ and end in ==). Then you can decode it in the command line with the following:
$ base64 -d -i picture.txt > picture.jpg
Open up picture.jpg, and you should see your smiling face!
Another interesting test you might try is the Metasploit browser_autopwn feature. The wiki gives a good job at describing how to run it here.
Conclusion
If you look at the source, all the page does is add in the hook.js file. The setup of BeEF is really slick. There just doesn’t seem to be anything terribly useful yet. It definitely shows the power of Ajax type of programming (in a good way), or how scary XSS can be (in a bad way). Hopefully it can grow into a more mature, useable project.