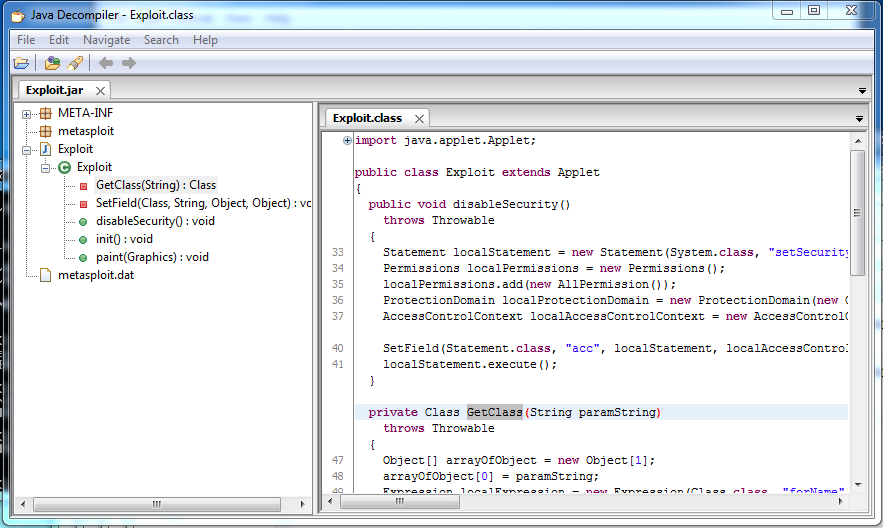
Sometimes Java Applets are compiled into .jar files, which can later be decompiled and dissected for valuable information that the author didn’t necessarily intend for you to have.
Setup Your Testbed
Any .jar file will do that you have lying around. I’m using one that Metasploit constructed from one of the (many many) recent Java exploits.
Attack
How do you find a vulnerable host?
If you see an applet is being served up by a .jar file, you can download that file to see what is on it.
How do you attack that host?
Download the file and load up your favorite decompiler. I prefer JD (get it? Java Decompiler), but really any one will do.
One great bit of information you can find in here is database connection information – location, username, password. From there, you can dump the contents of the database, or whatever other island hopping you can do.